Prelude VST #1: Will your computer quarantine a malicious Office document?
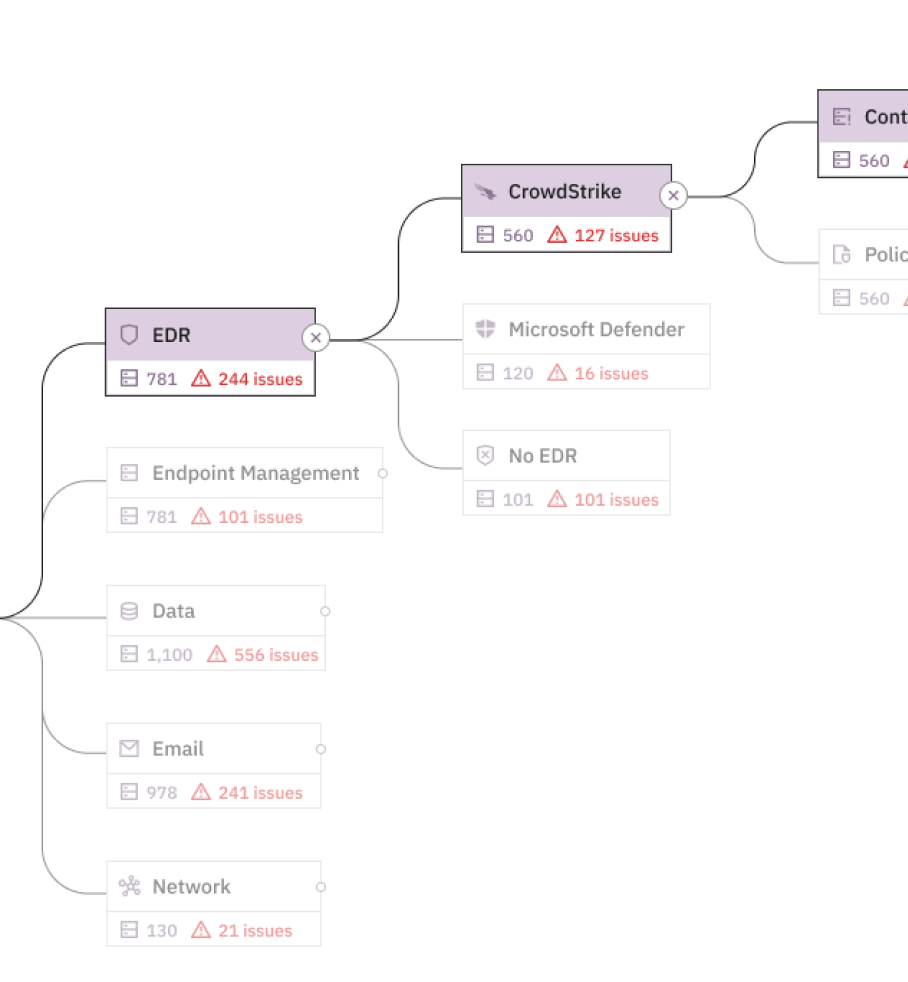
We rely on cyber defenses to protect us from the latest security threats, from our endpoints (antivirus, EDR) to our networks (IDS, firewalls). But how do we know they are actually protecting us?
Knowing how your defenses will react at this atomic level is security intelligence. And intelligence provides the insights you need to make decisions - becoming Actionable Security Intelligence. Knowing if you are protected - and if not - if you should care, enables you to allocate resources to the problem. Or not.
Without intelligence, we have no insights, and without insights, we are forced to make these decisions with partial, stochastic information. Or, unaware that a decision even needs to be made, potential risks pile up and it becomes impossible to distinguish between ‘hair on fire’ problems and false alarms, expending valuable energy and time.
Enabling Intelligence Across Your Infrastructure, with Prelude Detect
Detect is a security testing service that runs Verified Security Tests (VSTs) across your entire environment, safely and continuously.
See here for the technical specifications and the history behind VSTs.
Each VST produces a single piece of intelligence that can fuel a decision.
Today, Prelude is introducing our first open-source VST that is designed to be used on development and production endpoints across Windows, Mac and Linux environments. Our first published VST is titled: Will your computer quarantine a malicious Office document?
The test, which is open source, runs the following checks:
- Relevancy: Should this test run on a particular endpoint?
- Execution: A Microsoft Excel spreadsheet, containing a popular malicious macro, is dropped on the disk and it checks if any endpoint protections quarantine it.
- Clean up: The endpoint reverts to the state it was in prior to the test.
- Reporting: The results are sent to a centralized dashboard for review.
You can run the test yourself by following this walkthrough:
Because macros are connected to so many vulnerabilities and attack vectors, knowing if your defense successfully responds to a known signature provides a base layer of assurance.
But if your environment doesn’t respond well, you can make an informed decision:
- Should we install endpoint defense on those without one?
- Should we reconfigure the defense in areas that have protection but didn’t pass the test?
- Should we allocate people or technology to the area to investigate further?
- If the endpoint is vulnerable, are we willing to accept the risks of potential attack?
Being secure doesn’t mean resolving every vulnerability or defending against each behavior-driven threat. Being secure is relative to resource allocation and decision making. Without high-fidelity, ground-truth intelligence about the defensive state of your endpoints - it’s impossible to make high quality decisions. That’s why Prelude exists - to help your organization know with certainty that your defenses will protect you from the latest attacks.
—
Take the “Will your computer quarantine a malicious Office document?” VST for a spin by going to https://preludesecurity.com and following the instructions on any laptop or server.
Start monitoring controls free for 14 days