Ransomware attacks follow a predictable playbook: Encrypt files, then eliminate any possibility of recovery without paying the ransom. One of the first moves in this playbook is deleting Windows Volume Shadow Copies—the system's built-in backup snapshots that could otherwise restore encrypted files. CrowdStrike Falcon's "Volume Shadow Copy – Protect" setting is designed to block this tactic.
But enabling this protection isn't as simple as flipping a switch. Without proper configuration, you might inadvertently block legitimate backup software or system maintenance tools that also need to manage shadow copies. For IT administrators managing CrowdStrike policies across Windows endpoints, properly configuring and validating this protection is key to maintaining ransomware resilience. Here's what you need to know.
What Volume Shadow Copy–Protect does
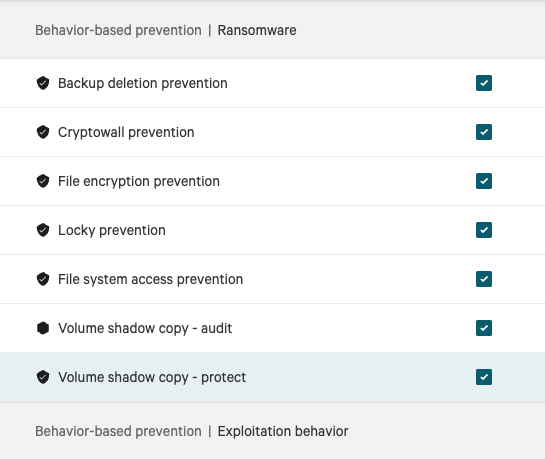
The Volume Shadow Copy – Protect feature in CrowdStrike Falcon prevents unauthorized processes from deleting Windows shadow copies. When enabled, it blocks common ransomware techniques like the vssadmin delete shadows command that attackers use to eliminate backup restore points.
This protection is built into CrowdStrike Falcon's behavior-based ransomware prevention capabilities. Enabling Volume Shadow Copy protection is highly recommended because ransomware commonly deletes shadow copies as one of its first moves during an attack. By design, ransomware wants to remove your ability to recover files without paying the ransom, so it will delete any VSS backups on the system.
The technique of deleting volume shadow copies via commands like vssadmin Delete Shadows /all /quiet is both pervasive and effective at inhibiting system recovery. When those backups are gone, restoring data becomes far more difficult, giving attackers significant leverage in ransom negotiations.
Why you should enable this protection
Shadow copy deletion is a standard component of modern ransomware operations. CrowdStrike's own analysis of LockBit ransomware demonstrates the stark difference between systems with Volume Shadow Copy protection enabled versus those without it. When the protection is active, ransomware loses one of its primary advantages: the ability to eliminate recovery options.
Enabling this setting provides several key benefits:
- Preserves recovery options by preventing unauthorized shadow copy deletion
- Reduces recovery time by maintaining accessible backup snapshots
- Minimizes data loss by keeping restore points available post-attack
- Decreases operational disruption by enabling faster system restoration
The protection works by monitoring for processes attempting to manipulate Volume Shadow Service (VSS) and blocking unauthorized deletion attempts while allowing legitimate system operations to continue.
Implementation considerations
Before enabling Volume Shadow Copy protection in a production environment, there are several important considerations:
Start with audit mode
Always run audit mode first to identify legitimate processes that interact with shadow copies. This includes backup software, system maintenance tools, and administrative scripts that may need to manage VSS snapshots. Enabling protection without this discovery phase can lead to unintended disruptions.
Configure allowlists
Based on audit mode findings, configure allowlists for expected processes before switching to protect mode. Common legitimate tools that may require exceptions include:
- Enterprise backup solutions
- System maintenance scripts
- Disk management utilities
- Database backup processes
License and platform requirements
Volume Shadow Copy protection requires a Falcon Prevent license and applies only to Windows endpoints. Ensure your licensing covers all systems where you plan to enable this feature.
Monitor for false positives
Some administrators have reported accidental blocking of backup scripts when exclusions weren't properly configured. Maintain monitoring during initial rollout to quickly identify and address any legitimate processes being blocked.
Test recovery procedures
After enabling protection, verify that protected shadow copies can actually be used for file recovery. Test the restore process on non-production systems to ensure the protection doesn't interfere with legitimate recovery operations.
How to verify that Volume Shadow Copyp
Confirming that Volume Shadow Copy protection is properly enabled across your environment can be done through several approaches, depending on your needs and infrastructure setup.
1. CrowdStrike Falcon Console
In the Falcon management console, this setting is toggled on a policy-by-policy basis. To review policies for this setting:
- Navigate to Prevention Policies > Windows > Ransomware Protection
- Locate the "Volume Shadow Copy – Protect" toggle
- Verify it's enabled (you'll also see a "Volume Shadow Copy – Audit" option for initial testing)
The policy interface clearly shows both audit and protect modes, allowing you to stage the rollout appropriately.
2. Via CrowdStrike API or IaC
For automated validation, query policies via:
- CrowdStrike's Python SDK for programmatic policy checks
- Pulumi or Terraform for infrastructure-as-code policy management
- CrowdStrike's REST API for custom integration workflows
3. On endpoint (test mode)
To validate the efficacy of the setting and inform any required detection logic, you can test on non-production systems:
- Attempt to run
vssadmin delete shadows /for=C:on a test machine - Falcon should block the command and generate an alert
- Verify the block appears in CrowdStrike's console logs
This testing confirms both that the protection is active and that alerting is working correctly.
4. Continuous monitoring with Prelude
For organizations managing large CrowdStrike deployments, our platform provides automated validation of Volume Shadow Copy protection settings, along with all other CrowdStrike prevention policies, across your entire environment. Rather than manually checking individual policies or endpoints, Prelude's platform continuously monitors whether this critical protection is enabled and properly configured across all managed systems.
This approach is particularly valuable for:
- Compliance reporting showing protection coverage percentages
- Drift detection when policies change unexpectedly
- Gap identification highlighting systems missing this protection
- Automated validation ensuring settings match security requirements

Volume Shadow Copy protection is a straightforward but critical defense against ransomware. The key is methodical implementation: audit first, configure exclusions, then enable protection. For larger environments, tools like Prelude provide the ongoing visibility needed to ensure this protection stays consistently configured across your fleet.


.jpg)
.jpg)