Picture this: your security team gets an alert about suspicious activity on the network. Investigation reveals it's coming from an unknown Windows laptop that's been accessing your file shares for weeks. No one in IT has ever seen this device before, it's not in your asset management system, and the user claims it's their "backup work laptop" they've been using from home. This scenario plays out daily in organizations worldwide—and it's exactly why unmanaged device detection has become critical.
With remote/hybrid work becoming the norm and employees increasingly using personal devices for business tasks, unmanaged and BYOD (Bring Your Own Device) endpoints have become one of the largest security blind spots in modern organizations.
According to Microsoft's Digital Defense Report, 80-90% of successful ransomware attacks originate from unmanaged devices—making the ability to identify and monitor these endpoints critical for any security program.
The challenge isn't just theoretical. Nearly half of all organizations now allow BYOD access to company resources, yet most lack comprehensive visibility into these devices. For IT and security teams, this creates a dangerous gap: You can't protect what you can't see.
Why are personal and rogue devices so difficult to pinpoint?
Unmanaged devices present a unique visibility challenge because they exist outside traditional IT oversight by design. Unlike corporate-issued laptops that are domain-joined, enrolled in Mobile Device Management (MDM) systems, and equipped with centrally managed security agents, BYOD devices operate in a gray area.
Several factors contribute to this visibility gap:
- Lack of centralized management: Personal devices aren't enrolled in corporate MDM solutions like Microsoft Intune or Jamf. They don't appear in Active Directory, and they often lack the endpoint detection and response (EDR) agents that provide visibility into corporate assets.
- Network invisibility: In hybrid work environments, BYOD devices frequently connect from home networks, coffee shops, or other remote locations. Traditional network scanning and monitoring tools that rely on devices being physically connected to corporate infrastructure miss these endpoints entirely.
- Privacy concerns: Employees are often reluctant to install corporate monitoring software on personal devices, creating a natural resistance to traditional asset management approaches.
- Authentication without enrollment: Modern cloud-first architectures allow users to authenticate to corporate applications without their devices being formally managed. A user can access Office 365, Salesforce, or other business applications from their personal iPhone without IT ever knowing the device exists.
This creates a fundamental problem: without visibility, there's no enforcement of security policies, patch management, or threat detection.
What are the security implications of unmanaged devices?
The security implications of unmanaged devices extend far beyond theoretical concerns. These endpoints frequently lack the layered protections that corporate devices receive, making them "open doors" for attackers looking to establish initial access.
Unmanaged devices typically miss several critical security controls:
- Patch and vulnerability management: Personal devices often run outdated operating systems and applications with known vulnerabilities
- Endpoint protection: Consumer antivirus solutions (if installed at all) provide significantly less protection than enterprise EDR platforms
- Configuration management: Default settings, weak passwords, and unrestricted admin access create additional attack vectors
- Monitoring and response: Without centralized logging and monitoring, security teams have no visibility into compromise indicators
This is particularly concerning for mid-market companies, which attackers increasingly target. Microsoft's data shows that 70% of human-operated ransomware victims have fewer than 500 employees—organizations that often have limited resources to implement comprehensive device management programs.
A multinational financial services firm faced exactly these challenges in their high-frequency trading environment, where configuration drift across security tools created dangerous gaps. As their IT Security Lead explained: "Within 10 minutes of deploying Prelude, we were diagnosing configuration drift across our security tools and identifying where we needed to focus both our technical and strategic efforts."
Method #1: Identity logs as a detection tool
Modern identity providers offer the first line of defense in identifying unmanaged devices. Platforms like Okta, Microsoft Entra ID (formerly Azure AD), and Google Workspace maintain detailed logs of authentication events, including device-specific information that can reveal BYOD usage.
When users authenticate to cloud applications, identity providers collect and store device fingerprints that include:
- Device names and identifiers
- Operating system versions
- Browser types and versions
- Network locations
- Device compliance status
Okta, for example, creates a unique device object for every registered device that accesses the service, providing visibility into what endpoints users are signing in from. Similarly, Azure AD can flag devices that are not domain-joined or compliant with corporate policies (Note: The specific conditional access policies need to be configured; it's not automatic flagging by default.)
Simple detection logic
The basic detection approach involves correlating user login events with your known device inventory:
- Export authentication logs: Pull login data from your identity provider showing all devices used for authentication over a specific timeframe (typically 30-90 days)
- Compare against asset inventory: Cross-reference device names and identifiers from authentication logs with your corporate device management system
- Flag discrepancies: Any device appearing in authentication logs but not in your managed asset list represents a potential unmanaged device
For example, if your authentication logs show 220 unique device names over the past month, but your corporate inventory only contains 200 devices, those 20 unaccounted devices warrant investigation. However, in practice, device naming inconsistencies across systems can make exact counts tricky.
Setting up conditional access
Many identity platforms allow you to create conditional access policies that flag or restrict logins from unmanaged devices. While blocking unmanaged devices entirely may not be feasible for BYOD-friendly organizations, these policies can at least generate alerts when unregistered devices attempt to access corporate resources.
Method #2: Aggregate and normalize inventory based on unique device identification
Device management platforms like Microsoft Intune, Jamf, or VMware Workspace ONE serve as the authoritative source for "known" corporate devices, but not the only ones. By treating these systems as your baseline and comparing against other data sources, you can identify gaps in your managed device coverage.
This includes aggregating inventory across endpoint-present tools like your EDR and vulnerability management platforms. Using a complete inventory allows you to identify gaps that are not easy to spot in a single tool and itemize devices that may be outside of traditional management.
The process involves several data correlation steps:
- Aggregate and normalize inventory: Combining assets from across various platforms gives you visibility into your endpoints, but requires normalization to account for which devices live across multiple systems. Many tools treat hostname differently, and these devices need to be matched across multiple tools to avoid counting the same device twice.
- Network infrastructure logs: Correlate this inventory data with DHCP logs, wireless access point connections, and VPN authentication records. Devices appearing on your network but not in your MDM represent potential security gaps.
- Application access logs: Review logs from business applications to identify devices accessing corporate resources outside of your managed inventory.
Practical implementation
A simple approach might involve:
- Weekly inventory export: Generate a report of all devices from your primary MDM platform and additional tools
- Network scan correlation: Compare this list against devices discovered through network scanning tools, DHCP logs, or firewall connection records that show devices accessing corporate resources
- Identity platform cross-reference: Match against authentication logs from your identity provider
- Gap analysis: Any device appearing in network, authentication logs, or your alternate tools but missing from your MDM requires investigation
Method #3: How Prelude automatically correlates multiple data sources
The most effective BYOD detection strategy combines all three data sources—identity platforms, device management systems, and network infrastructure. No single source provides complete visibility: an unmanaged device might never touch the corporate LAN but still access cloud applications, or appear on your network without authenticating to business applications.
Attempting to correlate data manually across multiple systems presents several challenges:
- Time-intensive process: Comparing hostname and serial numbers across multiple exports from network logs and disparate tools is time-consuming and error-prone, and adding identity platform data only compounds the complexity
- Data format inconsistencies: Different systems use varying device naming conventions and identifiers that add to potential error
- Timing mismatches: Devices may appear in one system before another, creating false positives
- Scale limitations: Manual processes don't scale effectively as organizations grow
Adding network infrastructure data from sources like Fortinet firewalls and Meraki wireless access points creates yet another layer of complexity, as these systems generate device connection logs with their own unique identifiers and timing patterns.
This is where what we’re building at Prelude provides significant value. By automatically integrating data from identity providers, MDM systems, and network infrastructure, our unified platform can highlight devices that appear in one system but not in others, thereby eliminating the manual effort while ensuring comprehensive coverage.
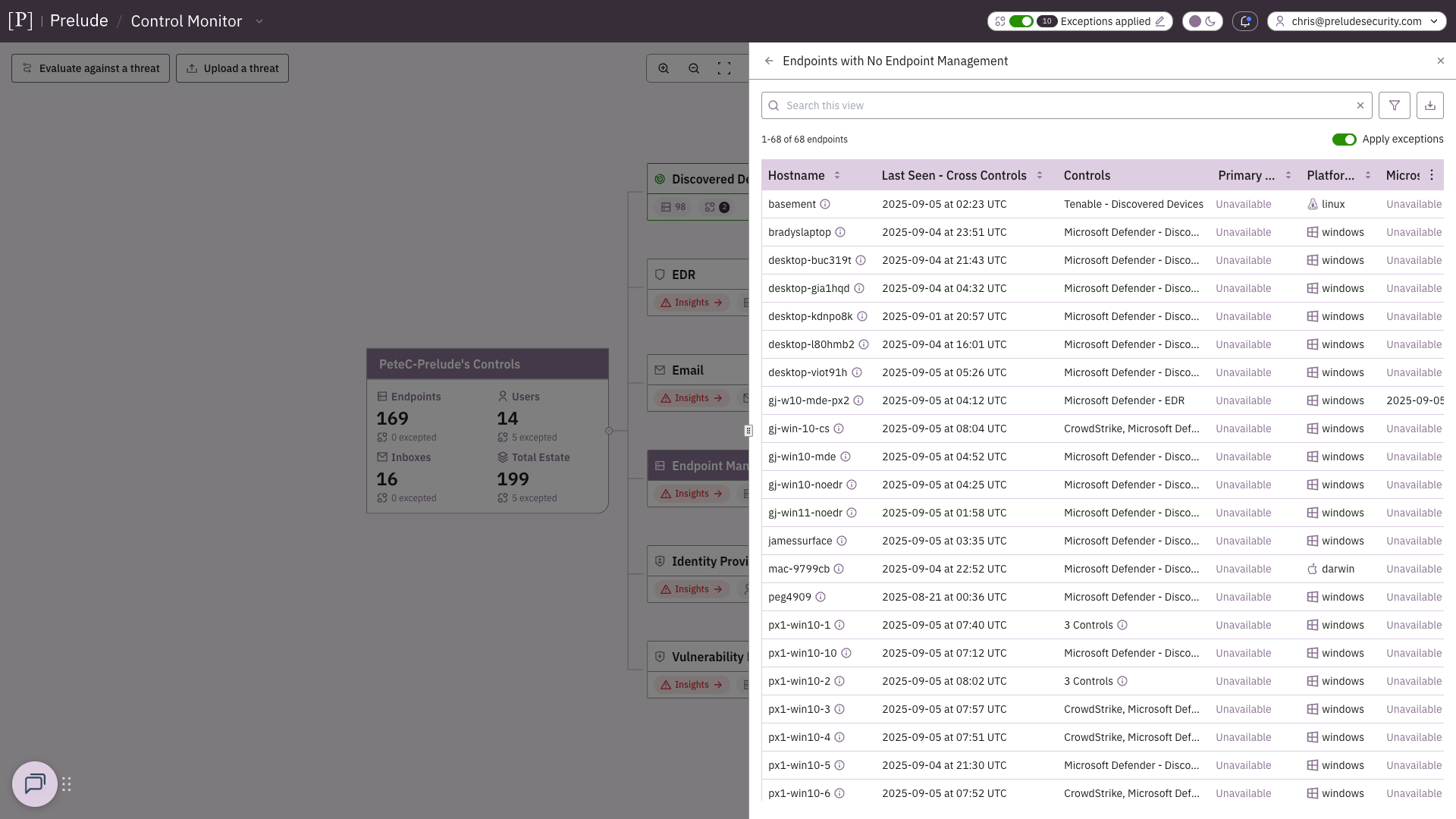
For example, if a device appears in Okta authentication logs and on your wireless network but isn't enrolled in Intune, that's a clear indicator of an unmanaged device requiring investigation. This automated correlation ensures unmanaged devices are identified quickly as they appear, rather than during periodic manual reviews.
For this financial services firm, our platform proved invaluable when they discovered a recently off-boarded employee's device was still accessible remotely without EDR protection—a potential insider threat that would have gone undetected without comprehensive device monitoring.
Effective unmanaged device detection requires persistent, multi-angle monitoring. Only through continuous correlation of identity, device management, and network data can organizations catch BYOD devices as they appear and preempt threats before they materialize.


.jpg)
.jpg)