Microsoft Entra ID Conditional Access policies serve as the enforcement backbone of Zero Trust security architectures, acting as intelligent gatekeepers that evaluate user, device, and contextual signals before granting access to corporate resources. For IT practitioners managing mid-market environments, these policies represent both a powerful security tool and a potential source of coverage gaps if not properly configured and monitored.
Despite their critical role, Conditional Access policies are frequently misconfigured, leaving organizations with false confidence in their security posture. Users may successfully access corporate resources without proper authentication controls, compliant devices, or adequate risk assessment, often without triggering any alerts for administrators. Understanding how these policies work, where they commonly fail, and how to validate their effectiveness is essential for maintaining robust Zero Trust enforcement.
How do Conditional Access policies work?
Conditional Access policies function as sophisticated if-then rules that evaluate multiple signals before making access decisions. When a user attempts to sign in or access a resource, Entra ID processes these policies in real-time, analyzing conditions like user identity, device compliance status, location, application sensitivity, and sign-in risk.
Policy structure and components
Each Conditional Access policy consists of two primary components:
- Assignments: Assignments define the scope of the policy—which users, groups, applications, and conditions trigger the evaluation.
- Access controls. Access controls specify what actions to take when the policy conditions are met, such as requiring multi-factor authentication, demanding a compliant device, or blocking access entirely.
The assignments section includes:
- Users and groups: Specific identities or organizational units subject to the policy
- Cloud apps or actions: Applications, services, or user actions that trigger evaluation
- Conditions: Contextual factors like sign-in risk, device platforms, locations, or client applications
Access controls can grant access with additional requirements (like MFA or approved client apps), block access completely, or require session controls such as app-enforced restrictions or sign-in frequency limits.
Policy evaluation logic
When multiple Conditional Access policies apply to a single sign-in attempt, Microsoft evaluates them using AND logic—meaning all applicable policies must be satisfied for access to be granted. This approach ensures comprehensive protection but requires careful policy design to avoid conflicts or unintended blocking.
Device-related conditions deserve special attention because they depend on accurate signals from Microsoft Intune or other mobile device management platforms. When a Conditional Access policy evaluates whether a device is compliant or hybrid Azure AD-joined, it's not performing this assessment independently—it's relying entirely on data provided by the device management platform.
A policy requiring compliant devices will only be effective if devices are properly enrolled, policies are correctly applied, and compliance status is accurately reported. Any breakdown in this chain can result in policy bypass or unexpected access denials.
What are the most common Conditional Access misconfigurations?
Real-world Conditional Access deployments frequently suffer from configuration drift and scoping errors that create security blind spots. These gaps often go unnoticed because they don't generate obvious failures—instead, they silently permit access that should have been restricted or controlled.
Incomplete scoping and coverage gaps
One of the most common issues is incomplete policy scoping that leaves certain users, applications, or scenarios unprotected. Guest accounts are frequently excluded from Conditional Access policies, creating a pathway for external users to access resources without proper controls. Similarly, administrators often forget to update policies when new applications are added to the environment or when organizational changes create new user groups.
Cloud application coverage presents another challenge. While organizations may have robust policies covering Microsoft 365 applications, they often overlook custom line-of-business applications, third-party SaaS tools, or recently added services. Each uncovered application represents a potential entry point that bypasses Zero Trust controls.
Device condition failures
Policies that require compliant or hybrid Azure AD-joined devices can fail silently when device enrollment or compliance checking isn't working correctly. Users may appear to have compliant devices in Intune while actually operating from unmanaged systems, or devices may fall out of compliance without triggering policy enforcement due to stale compliance data.
Platform compatibility also creates gaps. iOS and Android devices may have different compliance capabilities than Windows machines, and policies that work perfectly for corporate laptops may not translate effectively to mobile devices or personal equipment used in BYOD scenarios.
Legacy authentication bypass
Legacy authentication protocols like SMTP, IMAP, POP3, and older Exchange Web Services can completely bypass Conditional Access policies. These protocols don't support modern authentication flows, so they sidestep policy evaluation entirely. Attackers who compromise user credentials can leverage these protocols to access email and other resources without triggering MFA or device compliance requirements.
Many organizations unknowingly leave legacy authentication enabled, assuming their Conditional Access policies provide comprehensive protection. Without explicit policies to block legacy protocols, these authentication methods create a significant gap in Zero Trust enforcement.
Overuse of exclusions
Administrative convenience often leads to excessive use of policy exclusions. Break-glass accounts, service accounts, and VIP users are commonly excluded from Conditional Access policies to prevent lockouts. While some exclusions are necessary, they frequently become overly broad or remain in place longer than intended.
Location-based exclusions present similar risks. Organizations may exclude corporate IP ranges from certain policies, but this approach fails when users work remotely or when attackers operate from within the network perimeter. Exclusions based on named locations can also become stale as office locations change or network configurations evolve.
How do you validate Conditional Access policy enforcement?
Effective validation of Conditional Access policies requires proactive monitoring and testing rather than waiting for security incidents to reveal gaps. Microsoft provides several native tools for policy validation, but they require systematic use to be effective.
Analyzing Entra sign-in logs
Entra ID sign-in logs provide the most comprehensive view of policy evaluation and enforcement. Each sign-in event shows which Conditional Access policies were evaluated, whether they were applied successfully, and what conditions triggered or bypassed enforcement.
Pay particular attention to sign-in events showing "no policy applied" or "not applicable" results. These entries often indicate scoping gaps where users are accessing resources without any Conditional Access evaluation. Successful sign-ins that bypass expected policies deserve immediate investigation, as they may represent configuration errors or intentional exclusions that are no longer appropriate.
The sign-in logs also reveal patterns in policy failures. If users consistently fail device compliance requirements, it may indicate problems with Intune enrollment or policy distribution rather than genuine compliance issues. Similarly, frequent MFA failures might suggest policy timing issues or user training needs.
Leveraging the ‘What If’ tool
The Conditional Access What If tool allows administrators to simulate policy evaluation under different conditions without affecting actual user access. This tool is invaluable for testing policy changes before implementation and for understanding how existing policies will behave in specific scenarios.
Use the What If tool to test edge cases that might not occur frequently in normal operations. Simulate sign-ins from different device types, locations, and risk levels to ensure policies behave as expected. Pay special attention to scenarios involving guest users, service accounts, or emergency access situations.
Report-only mode for safe testing
Before enforcing new or modified Conditional Access policies, enable report-only mode to observe their potential impact without affecting user access. This approach allows you to identify unintended consequences, overly restrictive conditions, or gaps in policy logic before full enforcement.
Report-only mode generates log entries showing what would have happened if the policy were enforced, providing valuable insights into user behavior patterns and potential policy conflicts. Monitor these logs for several weeks to capture different usage scenarios and user populations before switching to enforcement mode.
Correlating identity and device data to detect drift
The most sophisticated security gaps emerge from drift between identity policies and actual device posture. Users may successfully authenticate with Conditional Access policies that require compliant devices while actually operating from unmanaged or non-compliant systems due to stale data, enrollment failures, or policy synchronization issues.
Effective validation requires correlating sign-in data from Entra ID with device compliance records from Intune or other mobile device management platforms. This correlation reveals discrepancies between what Conditional Access policies believe about device status and the actual compliance state reported by device management systems.
While this correlation can be done manually by exporting data from multiple platforms, the process is time-consuming and quickly becomes outdated.
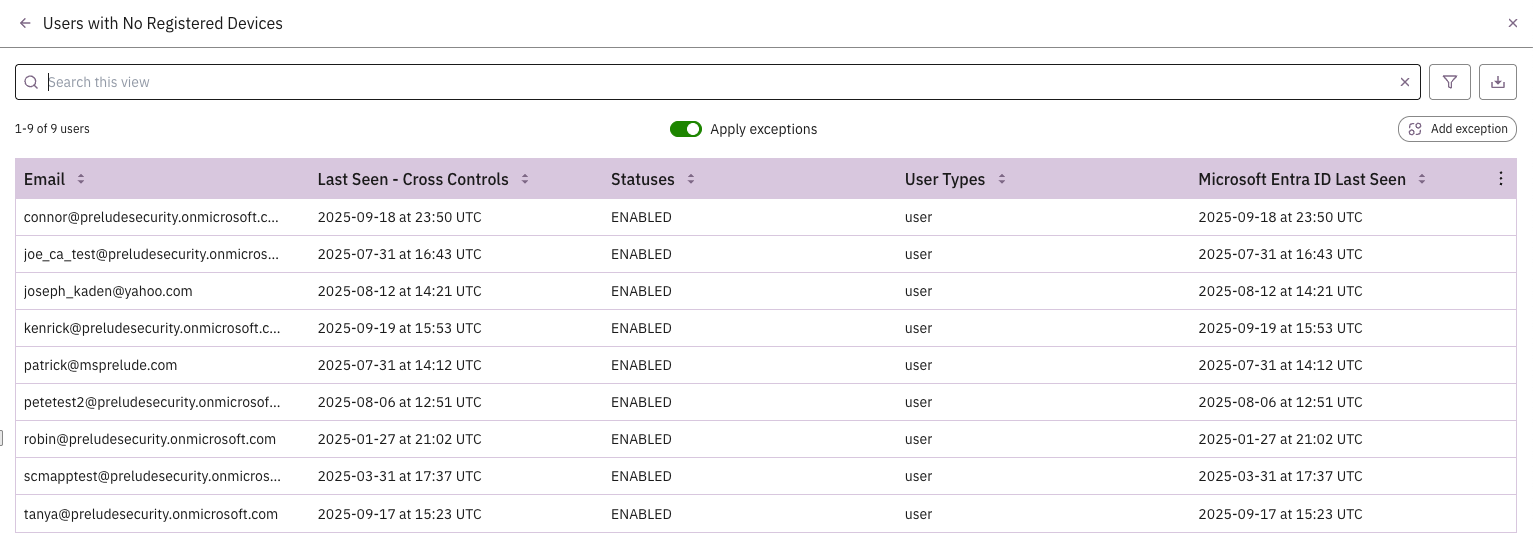
What we've built at Prelude automate this cross-platform correlation, continuously monitoring the relationship between identity policies and device compliance status to surface mismatches in real-time. These tools:
- Look for patterns where users consistently pass device compliance requirements in Conditional Access logs while showing non-compliant or unmanaged status in Intune. These mismatches often indicate synchronization delays, enrollment problems, or policy scoping errors that create enforcement blind spots.
- Monitor for newly added users who don't have appropriate Conditional Access policy coverage, devices that fall out of compliance without triggering policy enforcement, and applications that are added to the environment without corresponding access controls. These scenarios represent common sources of policy drift that can undermine Zero Trust implementation.
Conditional Access policies are powerful tools for implementing Zero Trust security, but their effectiveness depends on careful configuration, ongoing validation, and proactive monitoring for drift and gaps. The if-then logic that makes these policies flexible also creates opportunities for misconfiguration and coverage gaps that can undermine security objectives. Success requires treating Conditional Access as a continuous process rather than a set-and-forget configuration.
Organizations that invest in regular sign-in log analysis, systematic testing with native Microsoft tools, and correlation of identity and device data can achieve genuine confidence in their security posture. This level of assurance—knowing that access controls are consistently enforced across all users, devices, and applications—is essential for maintaining Zero Trust principles in dynamic, modern IT environments where the traditional network perimeter no longer provides meaningful security boundaries.


.jpg)
.jpg)
.jpg)