Visualize your entire IT security posture in minutes, not months
Transform how you evaluate your defenses with real-time visibility into the state of your security tools. Prelude automatically aggregates the insights you need to ensure your end-user devices are secure and policies are optimized.

Knowing if your environment is secure shouldn't be a distraction
Whether for insurance, compliance, or better assurance, control validation is an essential task for security teams, but one that takes time that most don't have. What if we could fix that?
Control validation
on your own
Jumping between consoles
Teams burn hours a week confirming coverage across dozens of security consoles from EDR to IAM, each with their own UI and logging format.
Spending cycles normalizing data
Reconciling multiple sources and schemas into one meaningful report means endless spreadsheet wrangling and chasing context, all which leaves more room for error.
Still missing blind spots
Despite doing this across countless hours, unmanaged devices can still slip through the cracks, providing a foothold to attackers and more work down the line spent on incident response.
Control validation
with Prelude
Seamlessly aggregate your inventory
Easy-to-use integrations rapidly consolidate your users and devices found across your security tools, surfacing critical gaps and misconfigurations within minutes of creating an account.
Achieve unparalleled visibility
Continuous monitoring and the integration of threat intelligence help teams manage exposure and identify gaps like unmanaged devices and configuration drift before attackers can exploit them.
Shift to proactive defense
Prelude keeps your team up-to-date on potential risk and control failures in-between the audits, so you can spend less time chasing evidence and more time securing your business.
How we maximize your tools while minimizing your effort
Prelude surfaces insights from the tools you already have in place to quickly find control coverage and configuration gaps for your end users. That means less time chasing answers, and more time securing the business.
Agentless visibility
Prelude offers read-only integrations with industry-leading device, network, and identity security platforms to power continuous visibility into the state of your security tools.
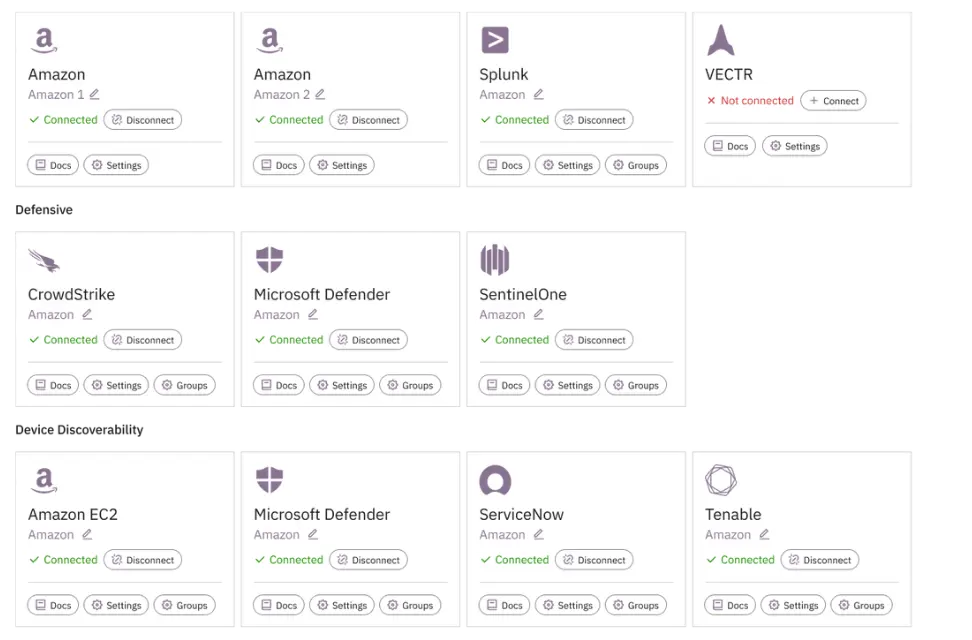
Aggregate inventory
By compiling and normalizing assets across your estate, Prelude presents a comprehensive view of your environment, inclusive of all users, inboxes, and devices.
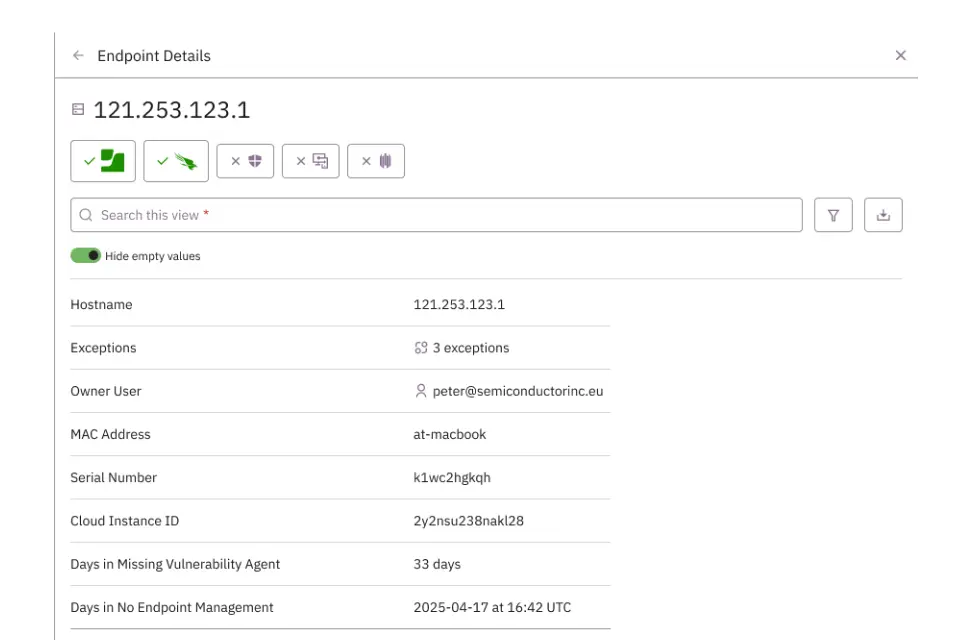
Gap analysis
Prelude constantly monitors your inventory against your expected controls and policy configurations, surfacing gaps and drift alongside risky users and devices, while delivering notifications to your service desk and communication channels.
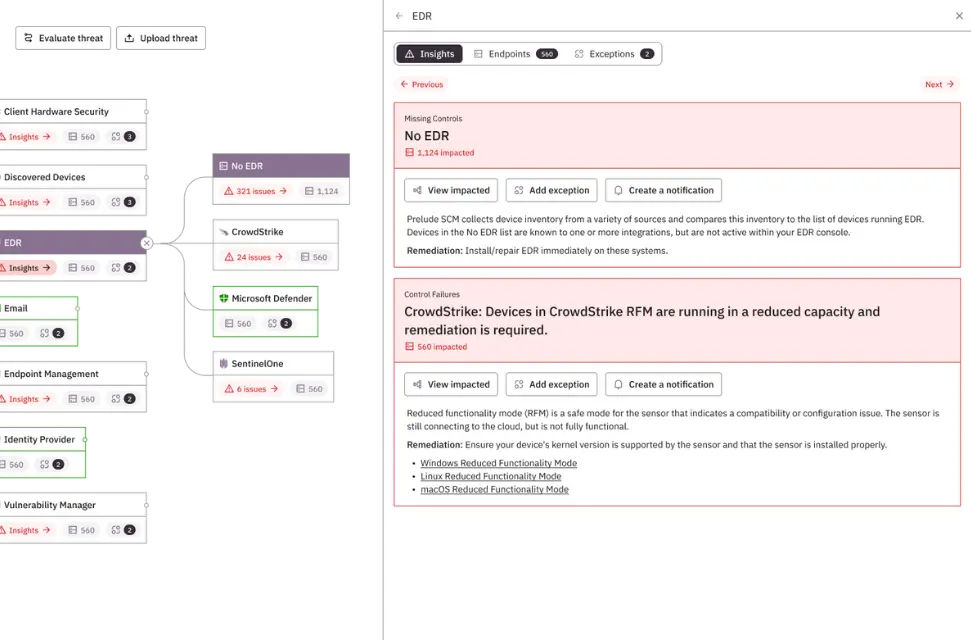
Exposure management
Your controls are automatically mapped to MITRE ATT&CK, so you can instantly layer the latest threat intelligence over your controls to understand the threats and techniques that present the most risk to your business, and where to target your remediation efforts.
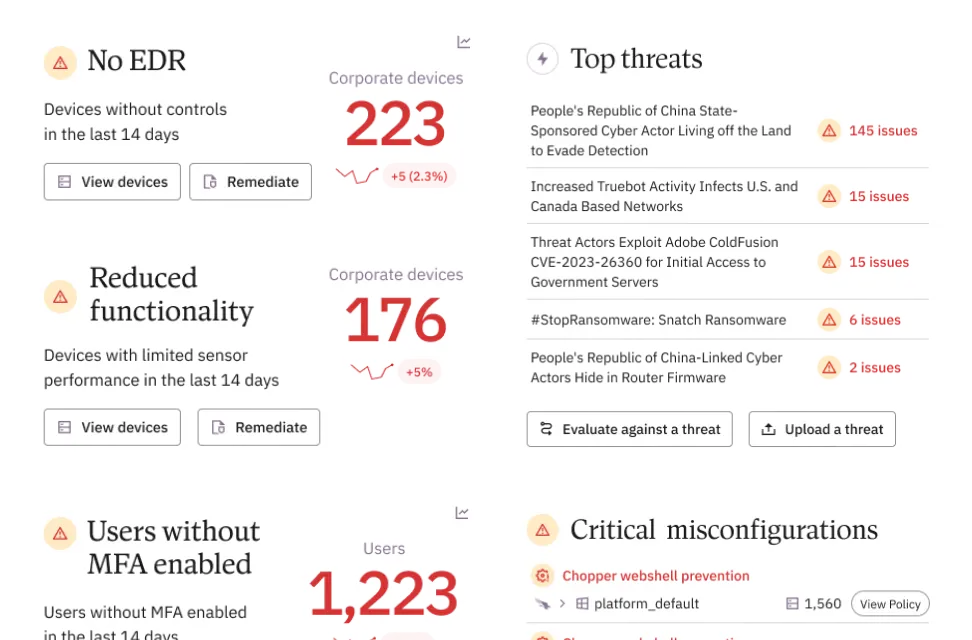
Take the guided tour
Within 10 minutes of deploying Prelude, we were diagnosing configuration drift across our security tools and identifying where we needed to focus both our technical and strategic efforts.





Augmenting your defenses with the tools you already have in place
Whether you're migrating between platforms, expanding your licenses, or want to maximize your best-of-breed platforms, Prelude connects with the tools you need to stay secure and ensures they're working as expected.






Reduce your critical exposure without wasting your precious time
What would you do with more time back in your day? Within minutes of creating an account, you'll uncover hidden coverage gaps, configuration issues, and risk exposure.


