If you’re leveraging Microsoft Entra ID (formerly Azure AD) to manage identities at your organization, you’re likely taking advantage of Groups. Groups allow security teams and systems administrators to organize users by role, department, and permissions.
These groups reflect how the business actually functions—and can be very handy to visualize where risk is concentrated. By syncing Entra ID groups into Prelude, you can view security posture through that same structure, making it easier to filter findings, understand configuration drift by team, and target remediation where it matters most.
What are Entra ID Groups (and where to find them)
Microsoft Entra ID Groups are collections of users that share similar access or policy needs in your organization. You may use groups to assign specific access or device policies in addition to simply organizing headcount in your IT environment.
Common examples include:
- Department groups such as finance, leadership, engineering, etc.
- Role- or permission-based groups such as global admins or helpdesk technicians
- Special-purpose groups such as service accounts, contractors, or executives
Entra ID groups can be found in the Microsoft Entra Admin Center → Groups, where each group shows its members, purpose, and associated access policies.
These groups already represent real security boundaries in your environment—which makes them a strong lens for understanding posture in Prelude where you can layer additional context such as EDR policies, InTune device compliance policies, and more.
Why use Entra ID Groups in Prelude
Syncing Entra ID groups into Prelude lets you evaluate security posture based on who is impacted, not just which devices are involved. By taking an user-first lens to your security posture, you can more easily prioritize technical and strategic efforts based on where the greatest risk is concentrated.
Consider the following use cases:
- Visibility based on users: See which teams or individuals are associated with missing controls or misconfigurations in group policies (e.g. Who on the engineering team hasn’t had a vulnerability scan in the last 14 days?).
- Prioritize based on risk: Prioritize technical and strategic efforts based on the added context of users, groups, and their associated risk. Is risk concentrated in executive workstations where critical IP and finance information is stored? Or on Identify where drift is concentrated (e.g., Executive workstations lacking EDR).
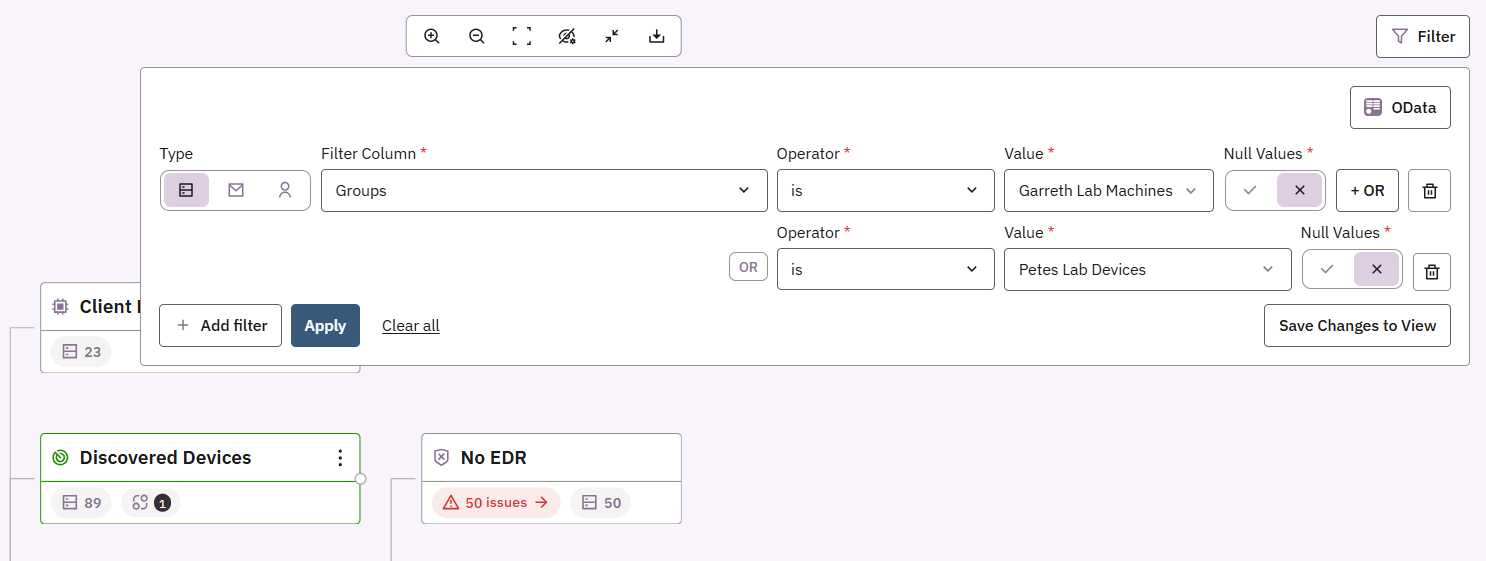
- Filter and segment findings: Narrow any report or view to a specific department, role group, or permissions to surface meaningful patterns.
- Cleanly scale exceptions : Apply exceptions to entire groups (e.g., third-party accounts) rather than managing device exclusions based on hostname or specific device criteria.
- Communicate posture clearly: Reporting by group aligns with how executives and compliance teams understand responsibility and level of impact.
This allows teams to move beyond a flat list of “issues” toward a structured understanding of who needs attention and where remediation effort should go.
How to connect Entra ID Groups to Prelude
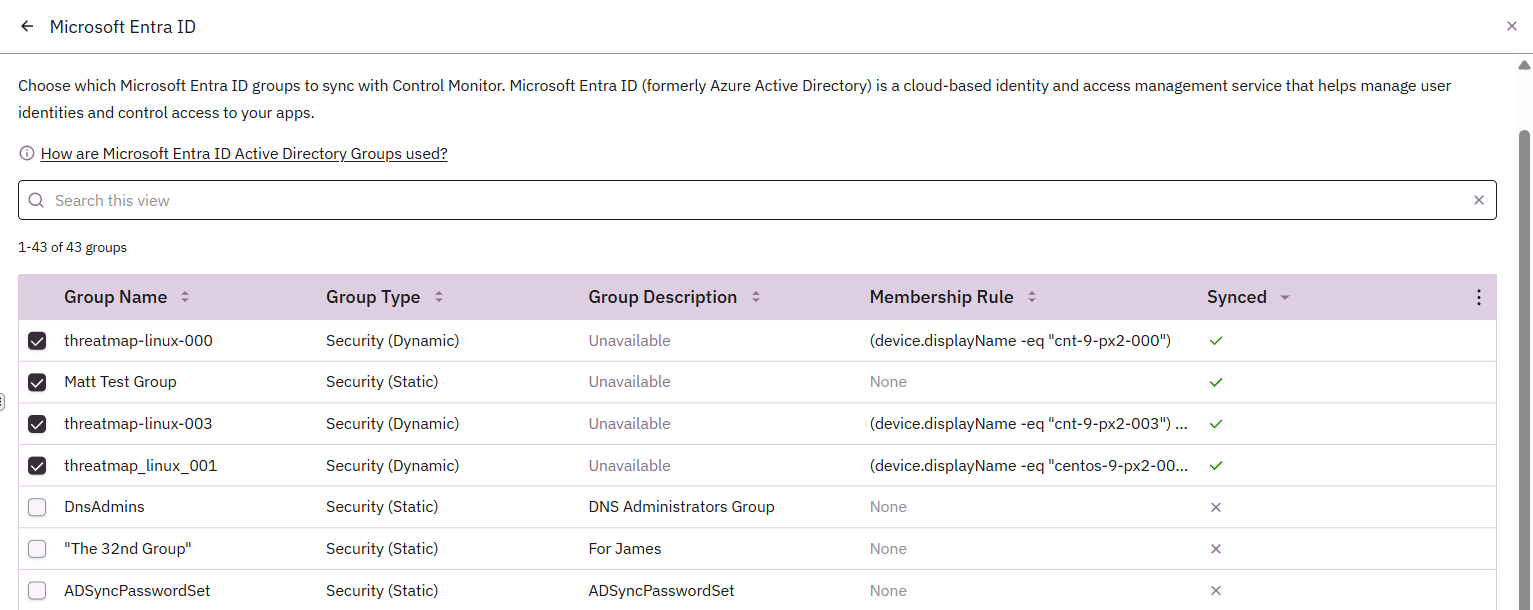
- In Prelude, go to Integrations → Microsoft Entra ID.
- If you have not already connected an account, authenticate using an account with the required directory read permissions
- Select the groups you want to sync.
Tip: Focus on operational groups, not every distribution or collaboration group. - Save the configuration. Prelude will begin to sync.
- Once connected, these groups can then be used as filters or conditions across the platform including exceptions, filters, reports, and notifications.
Any changes or exceptions to your synced groups in Entra ID (new hires, group changes, offboardings, etc.) automatically reflect in Prelude—no manual updates required.
If your organization already uses Entra ID Groups to structure access and responsibility. Syncing those groups into Prelude extends that structure into your security posture, making it easier to filter, prioritize, and act based on the added context. Start by identifying the groups that matter most for risk or organizing your environment—then use Prelude to see where coverage is strong, where gaps are concentrated, and how to remediate efficiently.


.jpg)
.jpg)
.jpg)