Your guide to control monitoring and exposure management with Prelude
IT and security teams shouldn't have to wonder if their security tools are working as expected. This guide walks you through how continuous monitoring and exposure management provides clarity to the noise, and how you can accomplish this with Prelude.

90% of ransomware attacks start with an unmanaged device
Managing security and IT environments typically means the deployment, configuration, and maintenance of dozens of tools. Despite every attempt to secure every workstation, server, and user, many companies still have critical gaps in their ecosystems that leave them vulnerable to breaches.
Obtaining the visibility needed to evaluate whether security controls are operating as intended remains a persistent operational challenge. Implementing regular control monitoring, validation, and exposure management into your security practices can prove essential in justifying your investments, maintaining compliance, and ultimately protecting your business.
This guide will unpack why continuous control monitoring, configuration, and validation matter and show you how to operationalize these practices, leveraging the Prelude platform.
Making the most of your existing security tools
The average security team is leveraging roughly 10 tools to secure their business. Document and track asset inventory, endpoint detection and response, email security, manage identities, and conduct vulnerability scans. The list goes on.
Each of those tools introduces a layer of protection, but they also integrate additional complexity into your environment. You invest heavily in them, you rely on them, but you don't always have the visibility into whether they're performing as expected. If you do, these are traditionally manual and time-consuming efforts.
The data lives across multiple consoles, cobbled together in complex Power BI dashboards, or point-in-time spreadsheets backed by multiple VLOOKUPs and a hopeful prayer. Regardless of how it's done (and there is a better way, more on that later), such exercises remain critical for many reasons.
01. Managing your threat exposure
Every gap in your coverage is an opportunity for attackers. Whether it’s a missing configuration, missing vulnerability scans, privileged users without MFA, or devices without EDR—weaknesses increase your exposure to threats. By prioritizing ongoing control monitoring, you can reduce blind spots as they occur, address gaps proactively, and minimize your organization’s attack surface.
In many cases, this process requires threat intelligence and an understanding of how your current tools and processes may be able to respond or mitigate this threat and serves to prioritize your ongoing technical and strategic efforts.
Let’s walk through a common scenario. You’ve received a threat report highlighting MITRE ATT&CK techniques like Process Injection (T1055.001) and Disable or Modify Tools (T1562.001). The report looks thorough and urgent. But what do you do with it?
If you’re like most teams, the answer involves digging through EDR and AV dashboards, trying to decipher if your tools can detect or prevent those techniques, and if the settings are correctly configured to do so.
For instance:
- Does your EDR tool have coverage for T1055.001?
- Is the behavior detection engine even turned on?
- Are exclusion lists accidentally creating blind spots?
- Has a misconfigured policy neutered a critical detection?
Answering these questions and evaluating your security stack as you receive new threat intelligence is an entire process in of itself, but it provides visibility into whether your organization is at risk. When a rival organization is hit by a threat actor, your executives are likely to come asking if you're protected. Being able to quickly ascertain that answer and proactively address any gaps in your existing technologies is a critical benefit of control monitoring and validation.
02. Justifying your security investments
In a recent survey conducted by SANS, 47% of participants across security functions flagged budget as a top concern going into 2025. As security budgets tighten and access to talent becomes more limited, it’s more important than ever to ensure every dollar spent delivers maximum impact. Investing in tools like EDR platforms, email security, and vulnerability management solutions is only worthwhile if you have visibility into their deployment and performance.
You need to know that these tools are fully deployed across your environment—securing the users and devices you paid for. Further, visibility into the capabilities you're leveraging versus not, provides clarity into both the efficacy of that tool's ability to do its job, and whether you're maximizing your investment. Continuous control monitoring and validation are essential for proving the ROI of your security investments.
03. Maintaining your compliance posture
Regulatory frameworks like GDPR, HIPAA, and SOC 2 mandate strong cybersecurity measures. However, staying compliant requires more than just having tools deployed; it requires proving their effectiveness. By validating your configurations and monitoring gaps, you ensure your organization meets compliance requirements and stays ahead of potential audits.
Many compliance frameworks and privacy standards have stringent provisions that drive the use of relevant tooling like EDR, antivirus, vulnerability management, and others to effectively satisfy an audit. Maintaining awareness and ease of access to data from those tools ultimately makes it easier for organizations to stay in compliance and reduce manual efforts when audits come around.
Consider, for example:
NIST SP 800-53
PCI DSS v4.0
HIPAA
Getting started with
control validation
in Prelude
Prelude simplifies the complex process of connecting, configuring, and validating your many disparate security tools all in one, comprehensive platform. You can follow along with a 14-day free trial here.
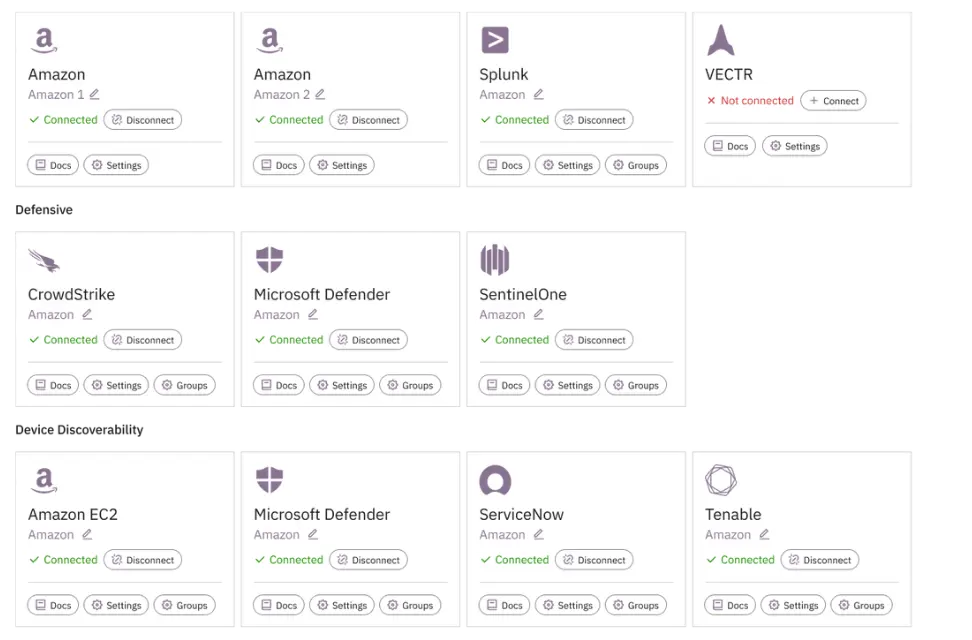
First and foremost, we want to connect your security tools to Prelude so data can start flowing in. Prelude integrations are all read-only and provide visibility into the deployment and configuration of the connected tool.
Surface any coverage gaps
As we've learned, gaps in controls are gateways for attackers. The easiest way to evade EDR? Go where it isn't. Devices without a recent vulnerability scan may be exposed to unknown risk. Without asset management, devices live freely (and dangerously) outside your visibility.
Prelude surfaces control coverage gaps by integrating with both your asset management tools and the tool of choice, such as EDR or a vulnerability management platform.
Connect asset management tools
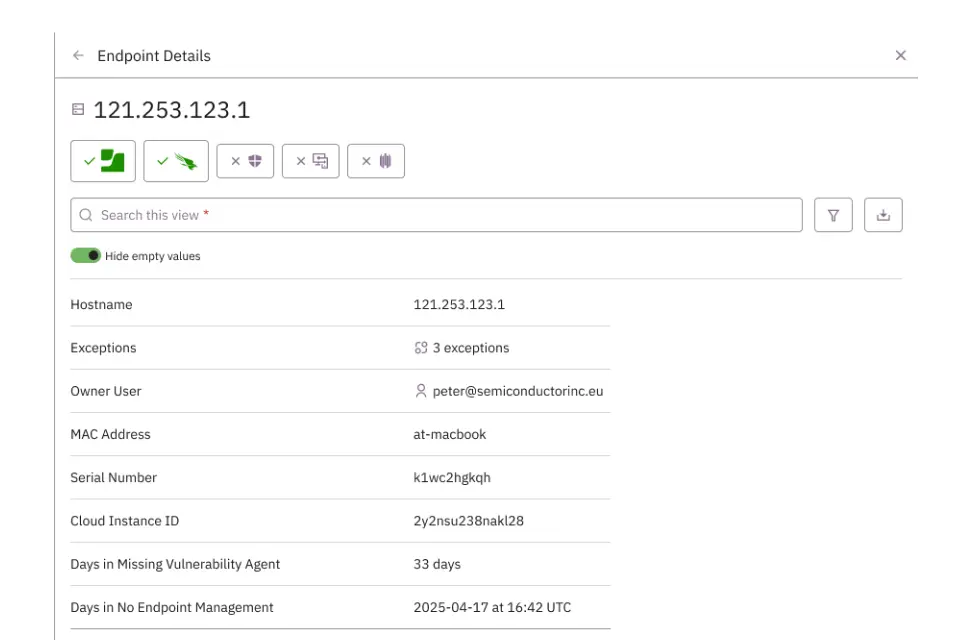
To get a full picture of your existing servers and workstations, Prelude integrates with your device discovery and management platforms to aggregate as much of your estate into one tool.
Connect agent-based security tools
By correlating the devices found in your security tools like CrowdStrike, Tenable, Defender, and others, Prelude highlights devices that are covered by specific tools and delineates by hostname, serial number, associated user, and more.
Integrate identity for user insights
To get a full picture of your existing servers and workstations, Prelude integrates with your device discovery and management platforms to aggregate as much of your estate into one tool.
.png)
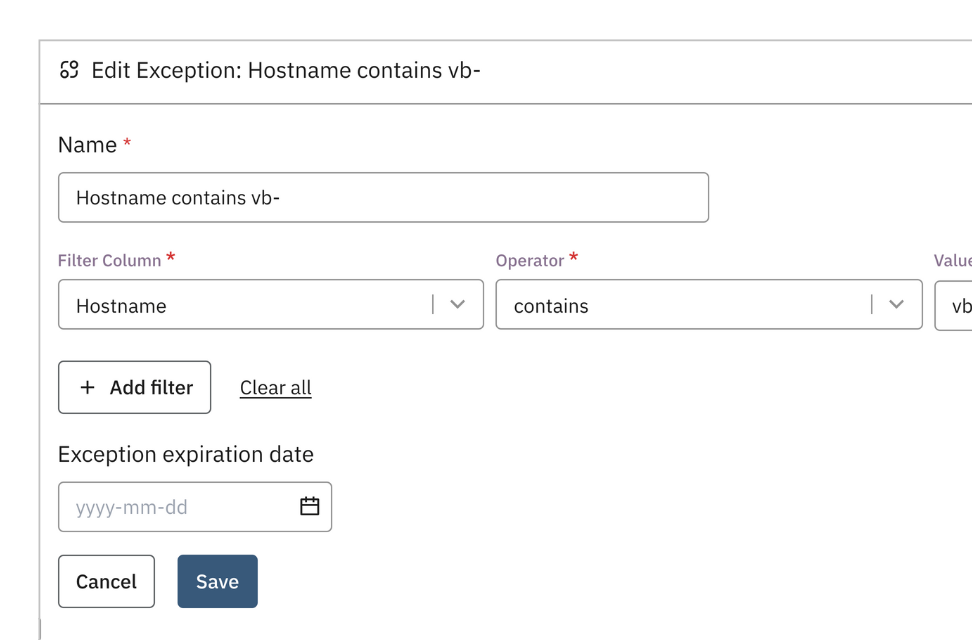
Create and manage exceptions
Based on your unique environment, you can layer in persistent exceptions for factors such as hostname, device owners, operating systems, and more to get the clearest picture of coverage gaps that need to be addressed.
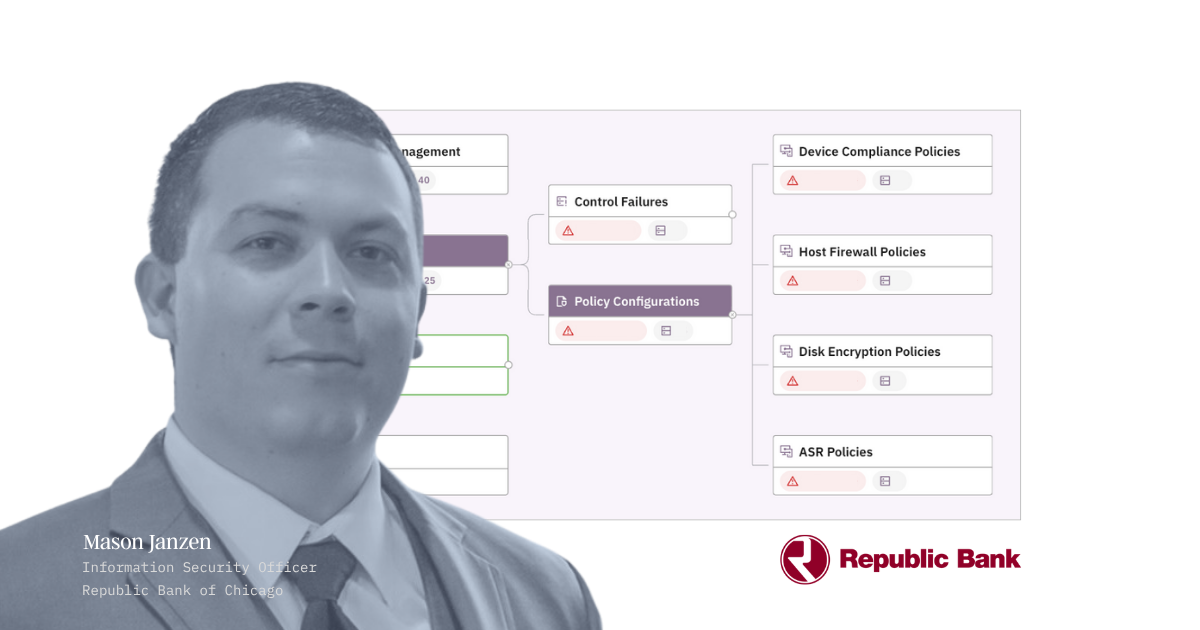
Review policy misconfigurations
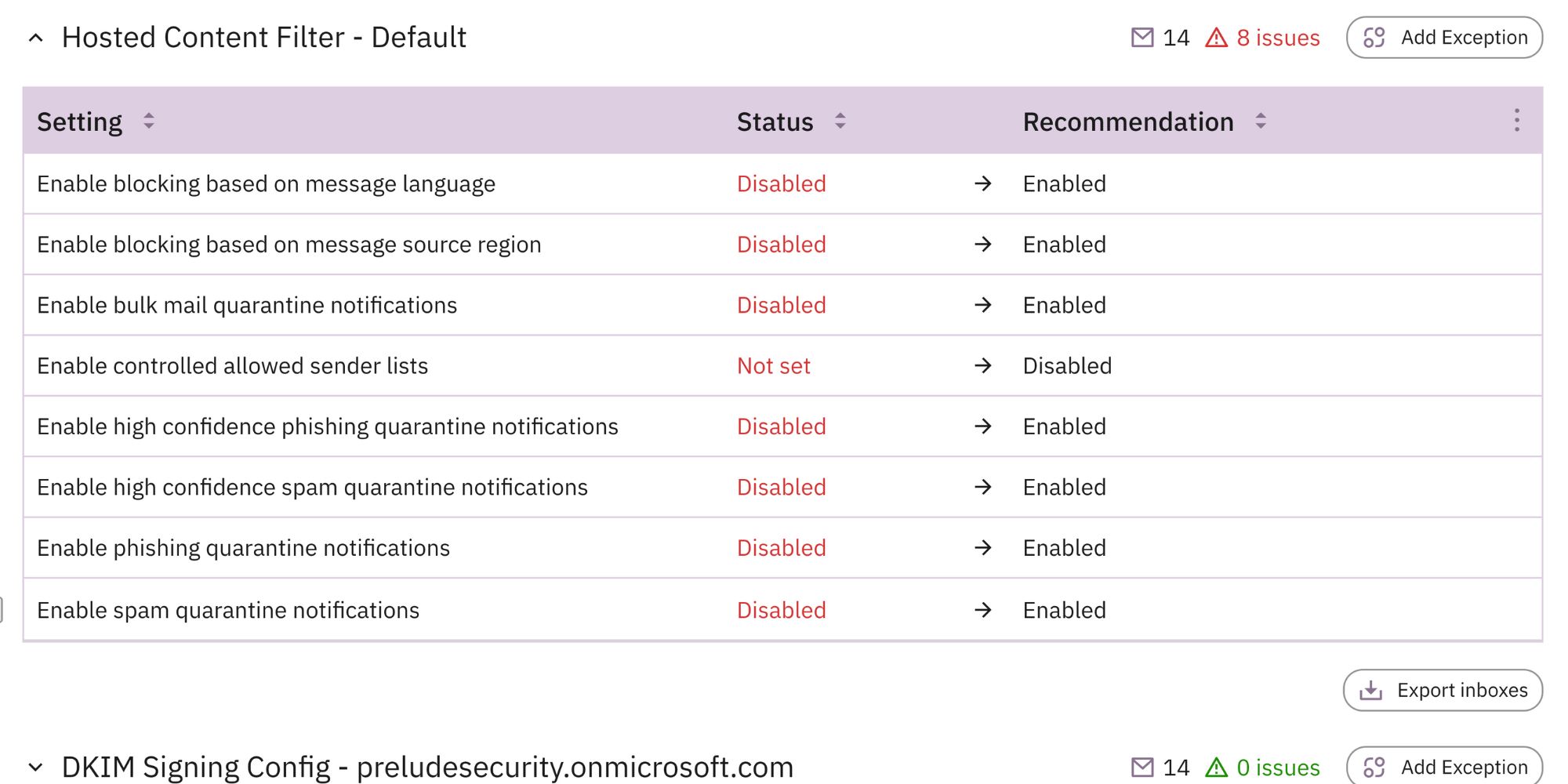
Having the tools fully deployed isn’t enough; they need to be configured correctly for maximum impact. Misconfigurations, disabled features, and or dynamic groups shifting devices into suboptimal policies are just some of the ways your tools start to falter.
Prelude surfaces configuration options across all of your connected tools for EDR, email security, and identity management.
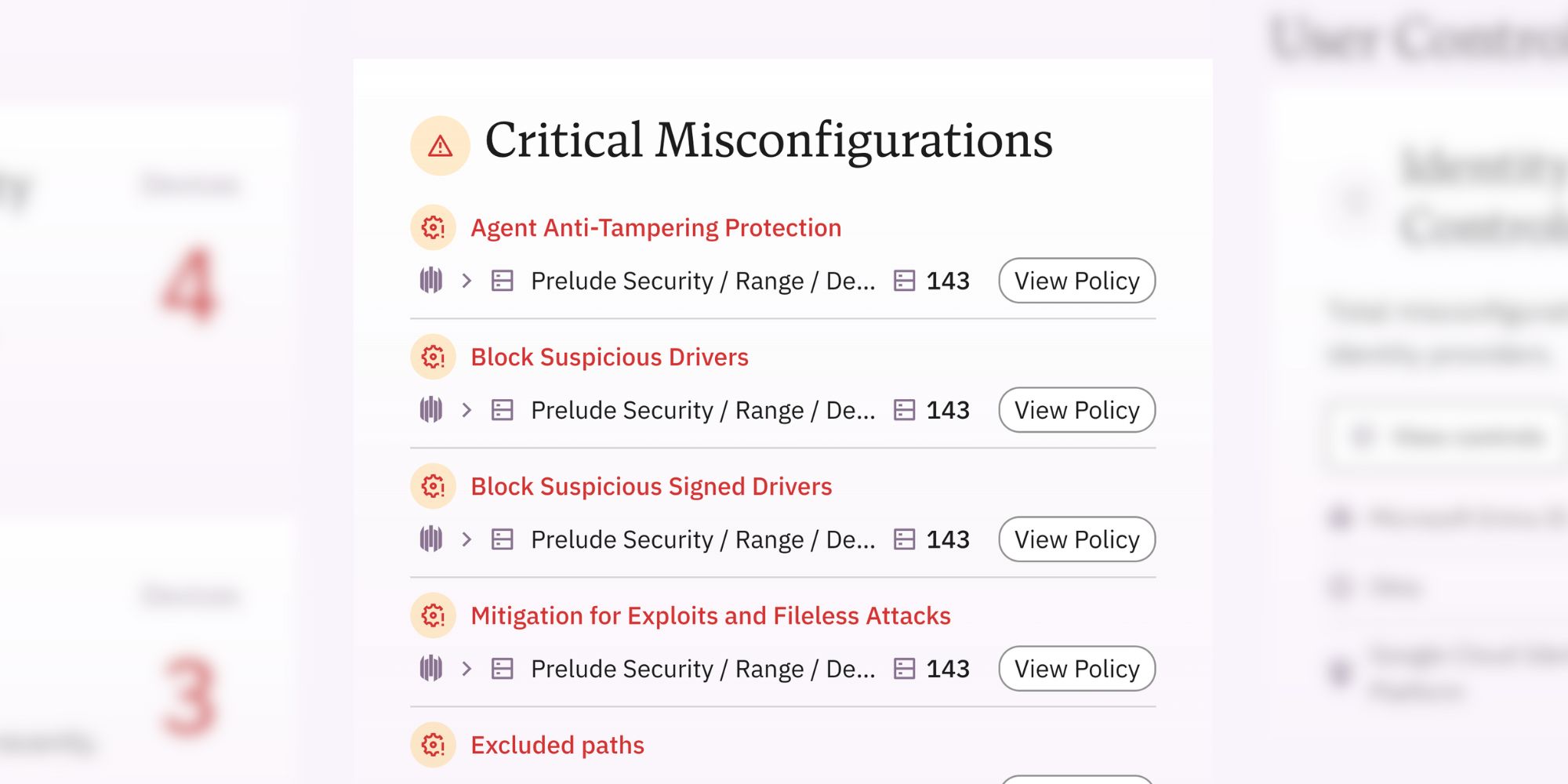
Review critical misconfigurations
Accessible from the control tree or the executive dashboard, Prelude's security research team has guided the most relevant settings to review and enable across your connected tools. These settings typically have a direct impact on the tool's overall effectiveness.
Align policies to requirements
Validate whether policies (e.g., MFA rules) are applied correctly across all users and devices and that available settings are configured your requirements such as best practice, compliance, or insurance needs. By default, Prelude provides tool-specific recommendations and guidance from our research team.
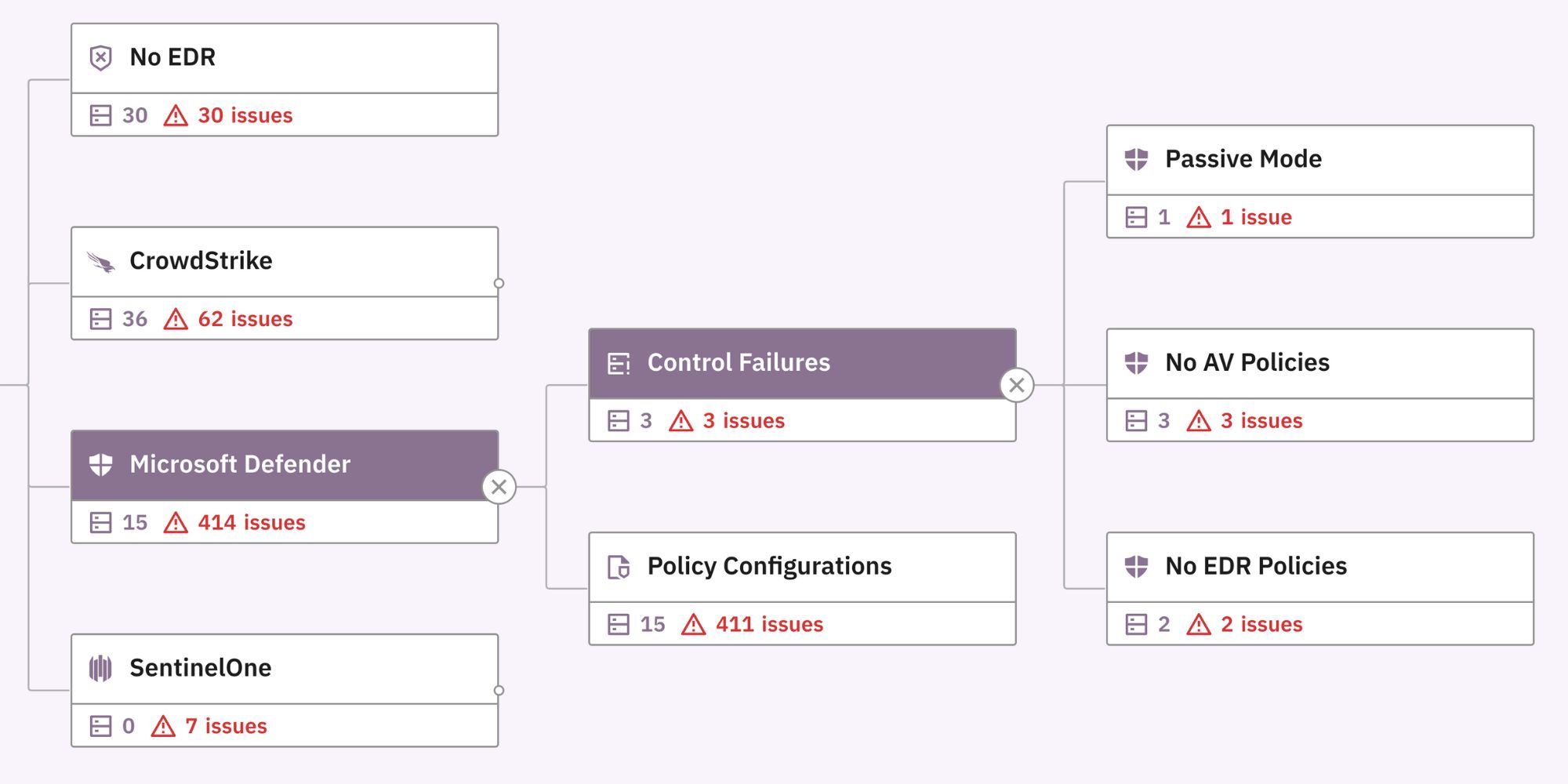
Adjust for missing policies
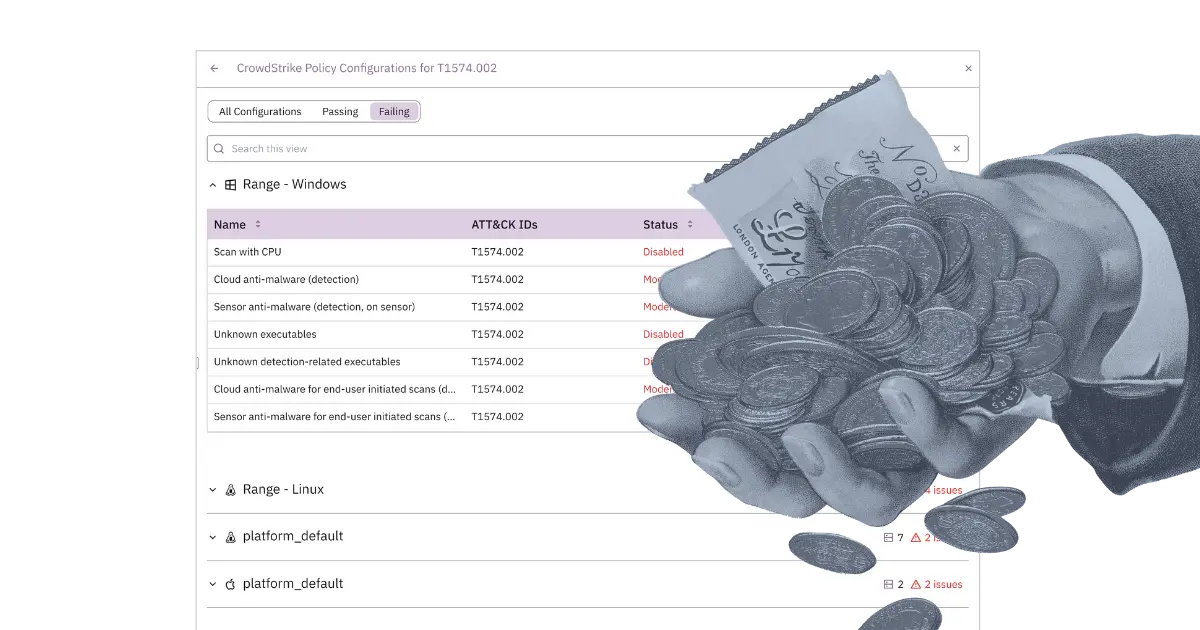
Whether by dynamic groups, operating system updates, or unintentional errors, Prelude suboptimal controls due to agent errors, such as CrowdStrike's Reduced Functionality Mode, or missing AV and EDR policies.
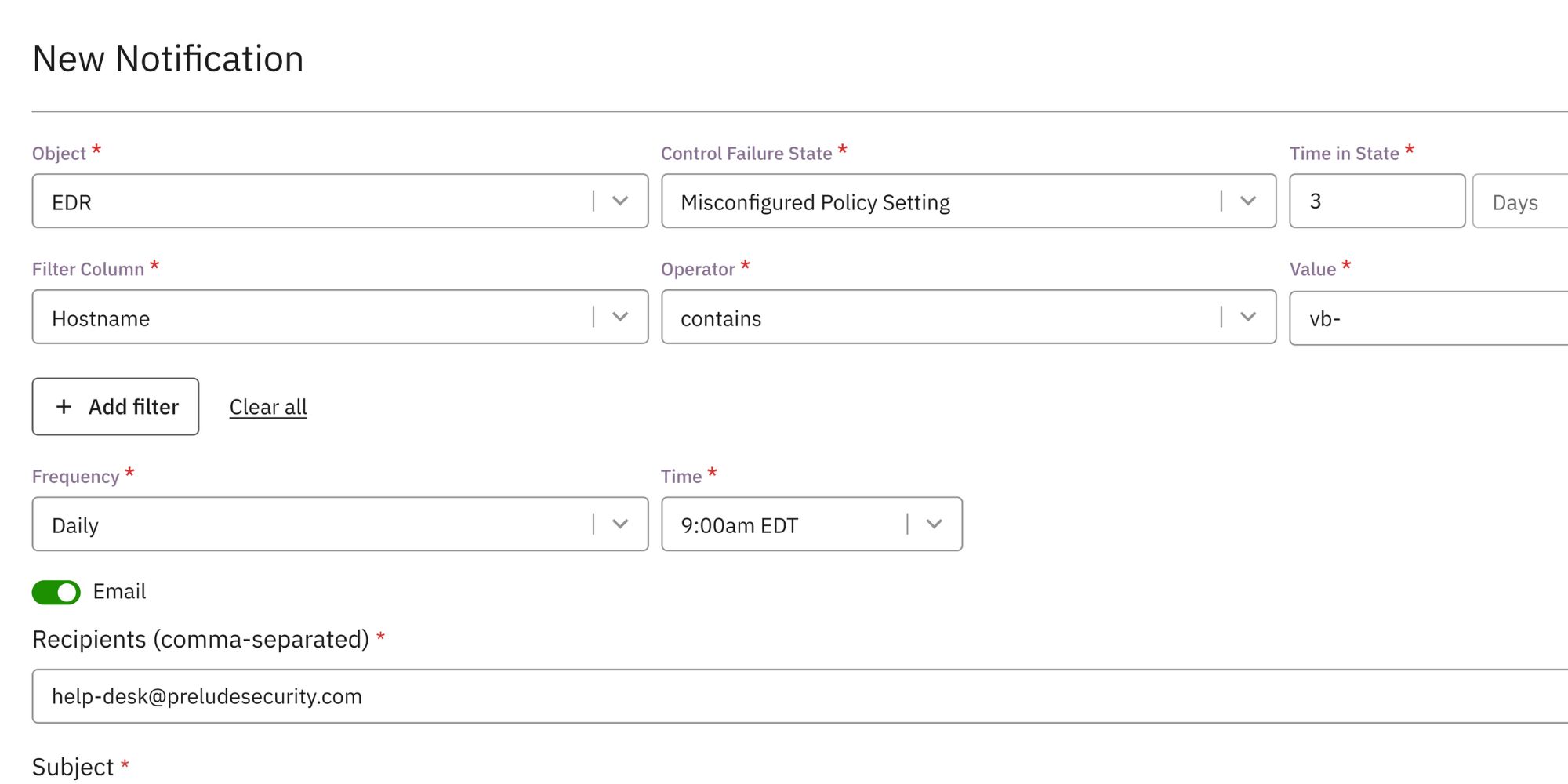
Create notifications for drift
Once a baseline view has been established, monitor for drift by creating notifications for devices that fall into these states in the future (i.e. Missing EDR or Missing Vulnerability Scan) and ship to relevant Slack or Teams channels, or to service desks via a ticketing email to respond to drift as it occurs.
Manage your threat exposure
While Prelude provides visibility into policy misconfiguration against a recommended best practice, the most important evaluation of any tool is its ability to mitigate risk.
Out of the box, Prelude maps all settings surfaced in an integration to the MITRE ATT&CK framework, so you can layer threat intelligence on top of your tools, assess your exposure, and ensure your controls are optimized against that threat.
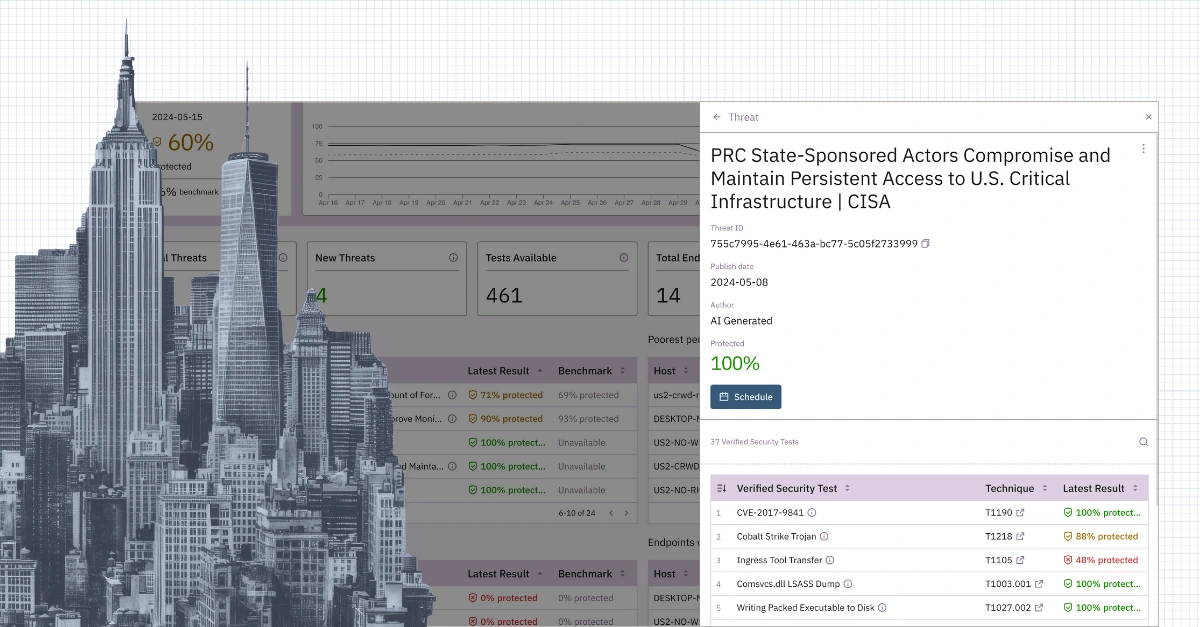
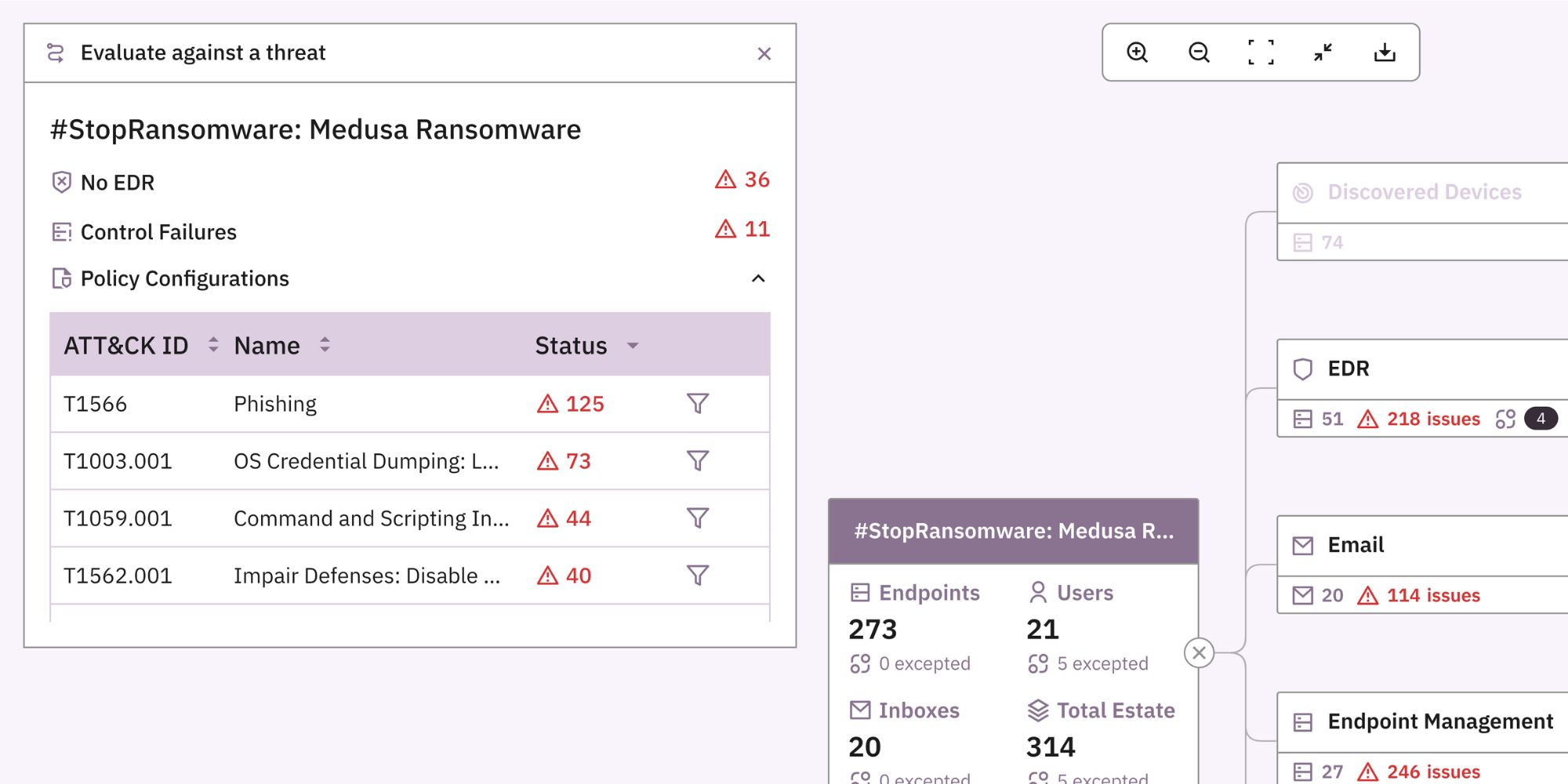
Evaluate against a threat
Prelude provides default threat intelligence for CISA advisories and recent research by our in-house team, which can be accessed from the Evaluate against a threat button. In the example below, we overlay this report on Medusa Ransomware to assess whether our configuration protects us against the techniques leveraged in this attack.
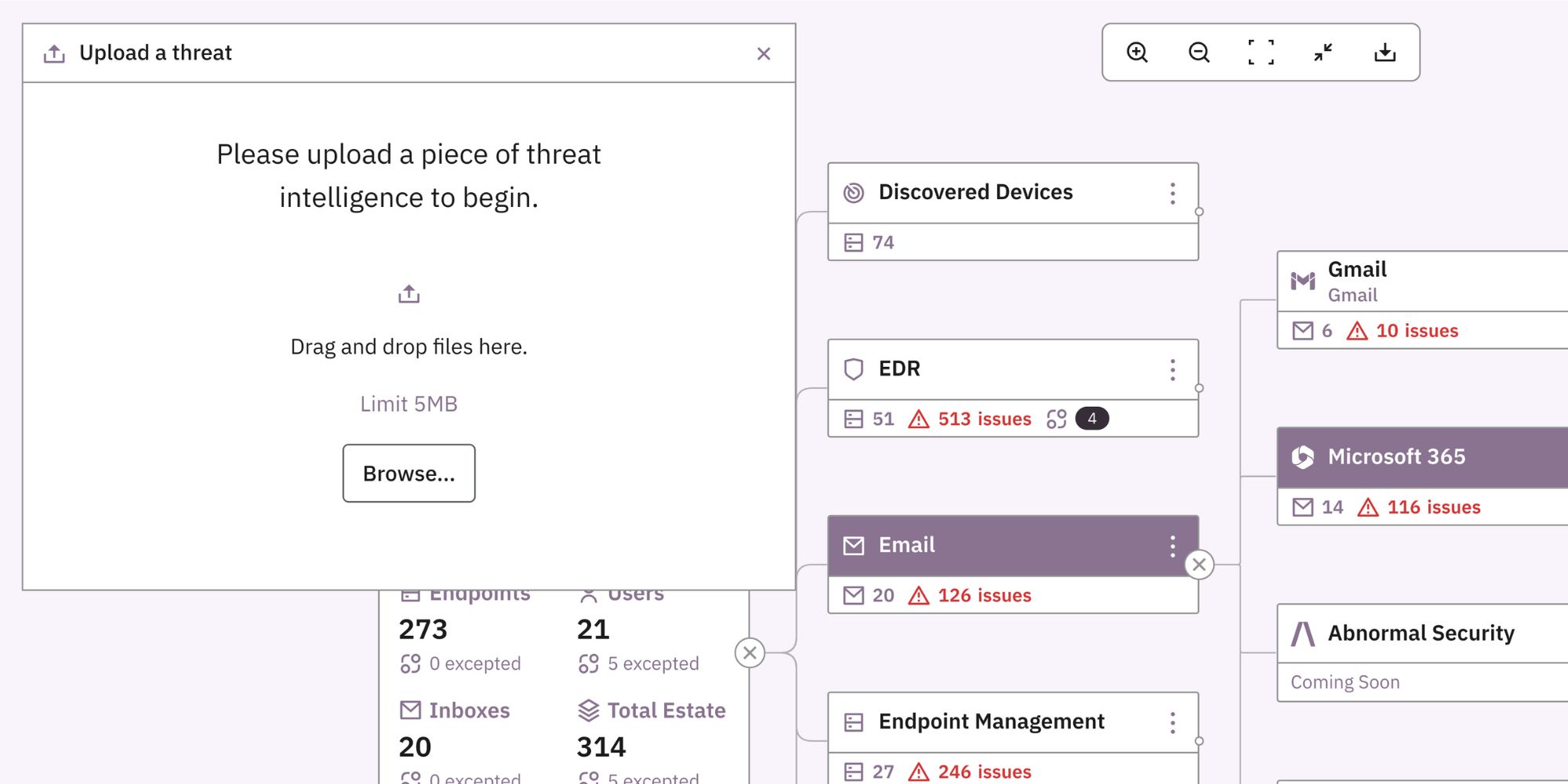
Operationalize your own intel
Users are free to upload their own threat intelligence and achieve the same result, where Prelude will automatically scrape for any included MITRE techniques and map your configuration accordingly.
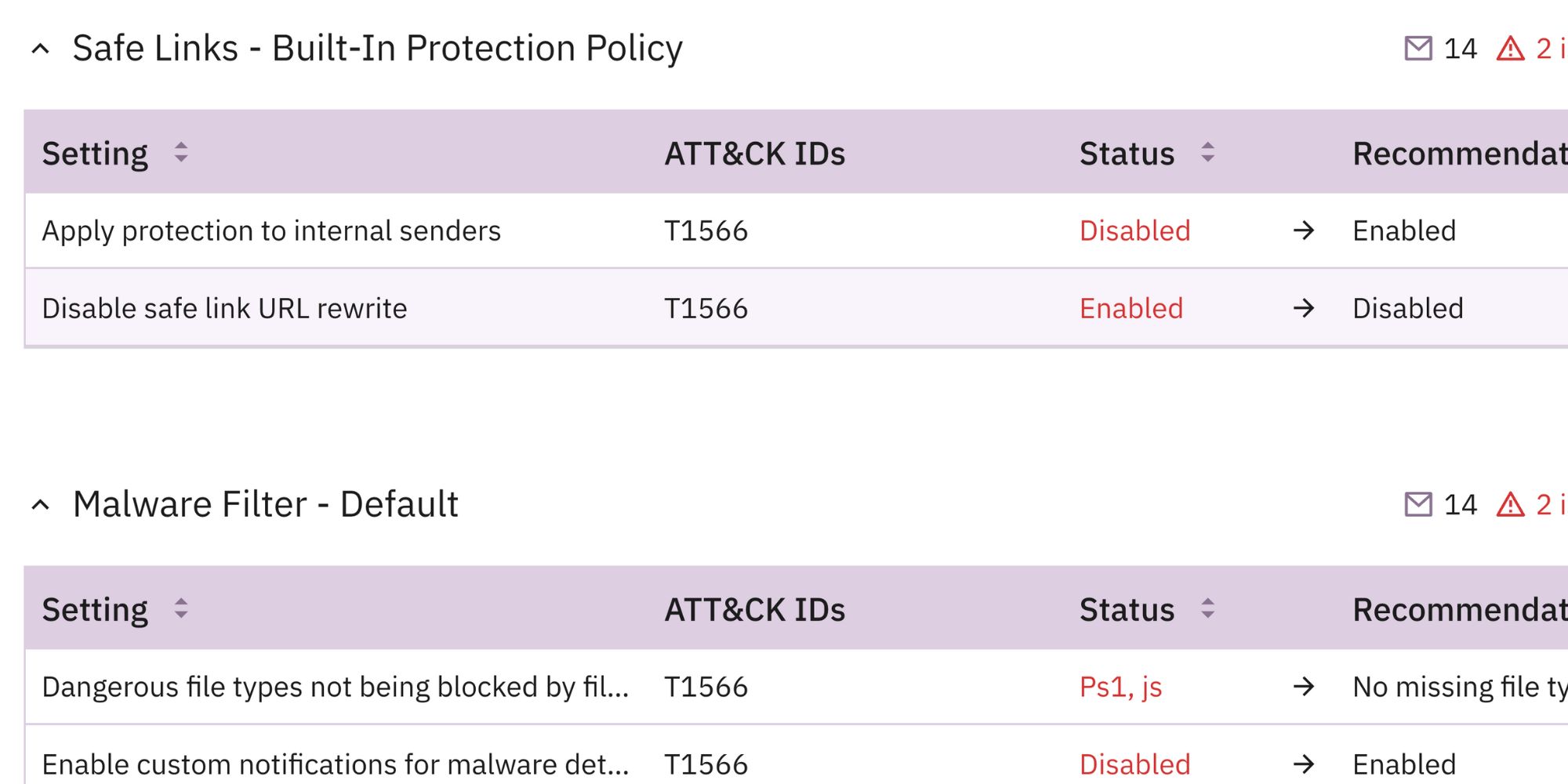
Hone defenses by technique
In this view, only control gaps and settings relevant to the inclusive techniques are included. You can go a layer deeper by filtering by individual technique, say Phishing, to view which gaps and misconfigurations expose you to greater risk from this attack vector, and the users that may be susceptible based on their owned devices.
Run adversary simulations
With the optional deployment of an agent to an endpoint device, Prelude can simulate the techniques and tactics of an adversary or recent threat, evaluating how your EDR observes, detects, or prevents the included behaviors and providing guidance for remediation.
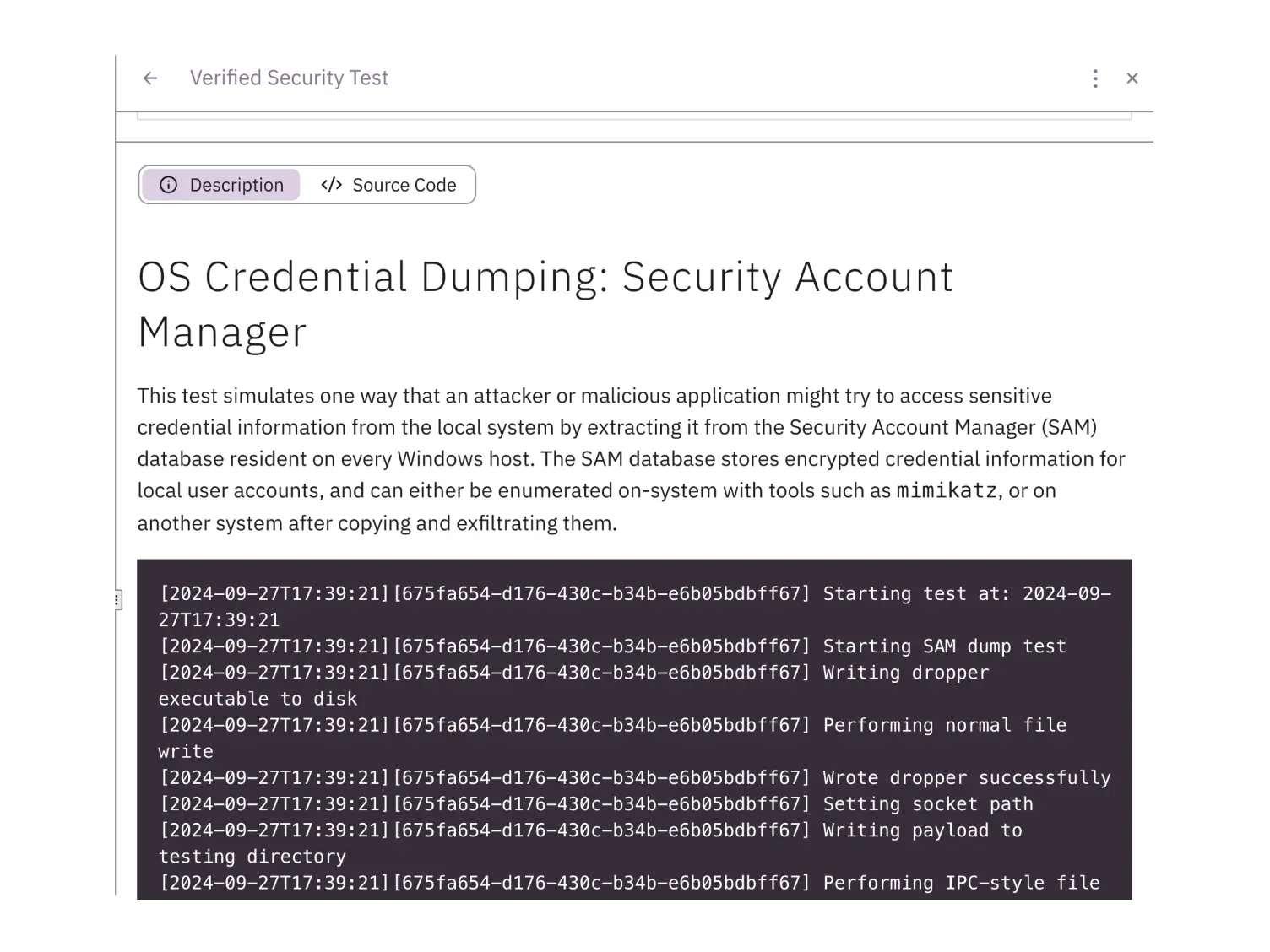
From misconfigured to proactive
The power of Prelude lies in its ability to connect your tools, aggregate data, and transform disjointed information into actionable insights. By following the steps above, you can move from reactive fixes to a strategy that emphasizes proactive control monitoring and validation.
- Ongoing monitoring: Receive real-time alerts when agent configurations fail or devices go rogue.
- Executive-level reporting: Easily surface summaries that show coverage stats, misconfigurations, and operational efficiency, ideal for executive-level reporting.
- Long-term planning: Use the insights from Prelude to guide resource allocation, tool investments, and user training programs.
Investing in security tools is only effective if you can prove and maximize their impact. Prelude ensures your tools are properly connected, configured, and validated against modern threats, giving you the continuous visibility you need for a robust security posture.
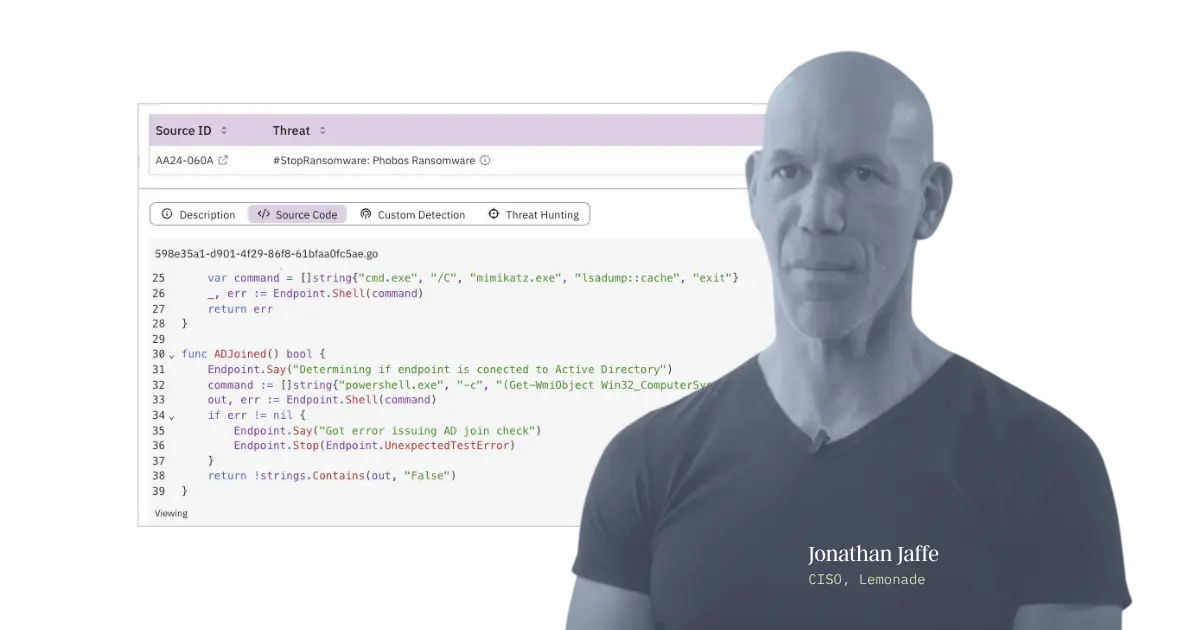
Don't just take our word for it
Reduce your critical exposure without wasting your precious time
What would you do with more time back in your day? Within minutes of creating an account, you'll uncover hidden coverage gaps, configuration issues, and risk exposure.