.jpg)
Security
What Are the Key Risks of Deploying Local AI Agents in Business Environments?
Learn the 4 critical risk categories when deploying AI agents locally vs cloud: data privacy, security, compliance & operations.

Chris Singlemann
Go-to-market
Security
Artificial Intelligence
.jpg)
Endpoint Security
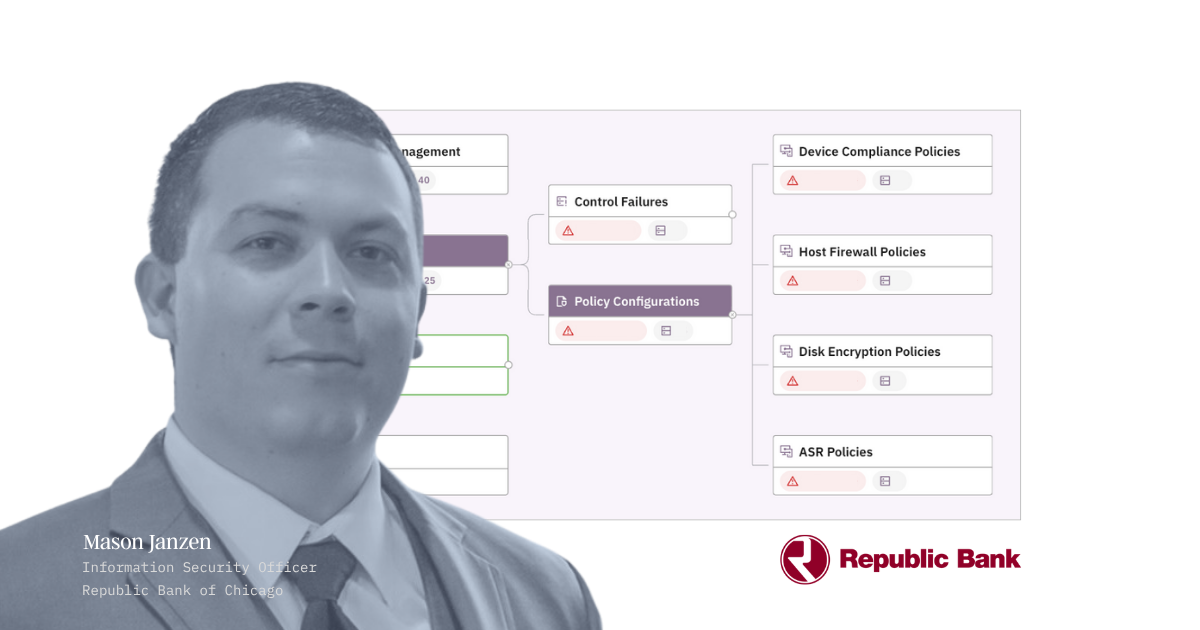
How IT Asset Management Enhances Cyber Security
Learn how IT asset management strengthens cybersecurity through automated discovery, vulnerability prioritization, and compliance.

Pete Constantine
Product
Endpoint Security
Security
Platform

Endpoint Security
It's (Finally) Time For The Next Generation of Endpoint Security
As antivirus innovated between 1995 and 2010, and EDR between 2010 and 2025, a new generation of endpoint protection is needed to combat modern ransomware.

Spencer Thompson
Leadership
Company
Security
Endpoint Security

Security
How to Make Cyber Insurance More Than Security Theater
The technical controls required for cyber insurance shouldn't just be about checking the box. Constantly monitoring and validating those tools is the difference between real resilience and your claim not getting paid out.

Spencer Thompson
Leadership
Cyber insurance
Control Validation
Security

Security
The Security Questions You Should Always Be Able to Answer
From device management to MFA enforcement, understanding how your environment is secured at any given time is a critical element for insurance and audits.

Chris Singlemann
Go-to-market
Control Monitoring
Control Validation
Security
Identity Security
Endpoint Security

Security
How Lean Security Teams Can Build Resilient Defenses
Operationalizing continuous control monitoring and threat exposure management doesn't need to be a drain on your team.

Chris Singlemann
Go-to-market
Control Validation
Control Monitoring
Security

Control Monitoring
Building a Continuous Threat Exposure Management (CTEM) Program at Your Business
Deploying a robust CTEM program can reduce operational load while mitigating your risk against an increasing number of vulnerabilities.

Chris Singlemann
Go-to-market
Control Monitoring
Security
Security Testing
.jpg)
Security
Four Takeaways From My Fireside Chat With Matt Hand
Matt Hand, Director of Security Research and author of "Evading EDR" provides their perspective on their career and the future of security control validation.

Chris Singlemann
Go-to-market
Control Validation
Security
Company

Endpoint Security
Five EDR Prevention Policy Settings That Should Always Be Enabled
Endpoint detection and response tools are often black boxes of opaque policies. Our experts provide the critical insight into policies you should always have enabled in your platform.

Chris Singlemann
Go-to-market
Control Monitoring
Security
Control Validation
Resources
Insights to help you manage your security posture
See for yourself
Done with reading for the day? Try Prelude instead.
Put our insights to good use with a free trial of Prelude so you can validate the coverage, configuration, and efficacy of your security tools.



.jpeg)