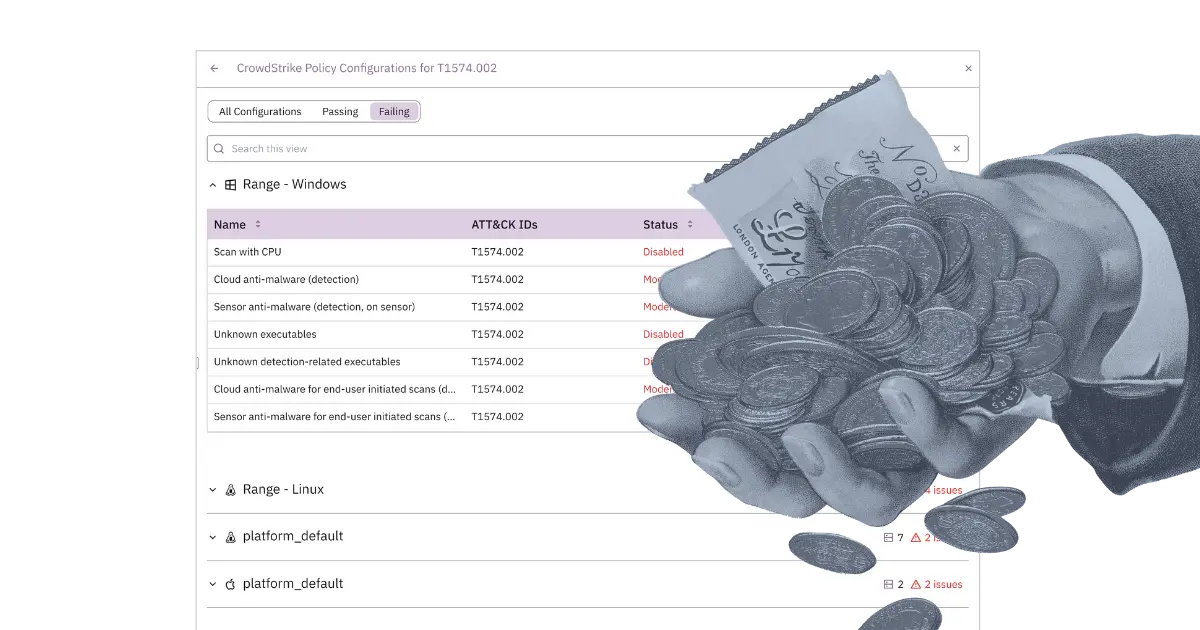
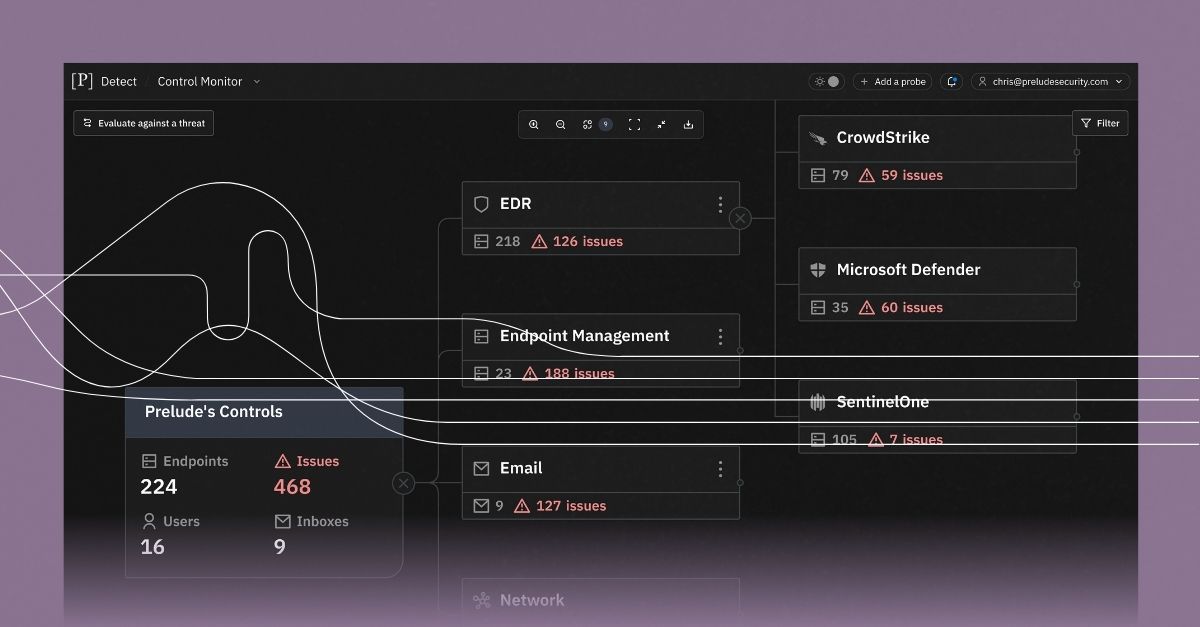
Resources
Helping you make the most of the security tools you already have
Get the latest insights and expertise on security from the team behind Prelude.
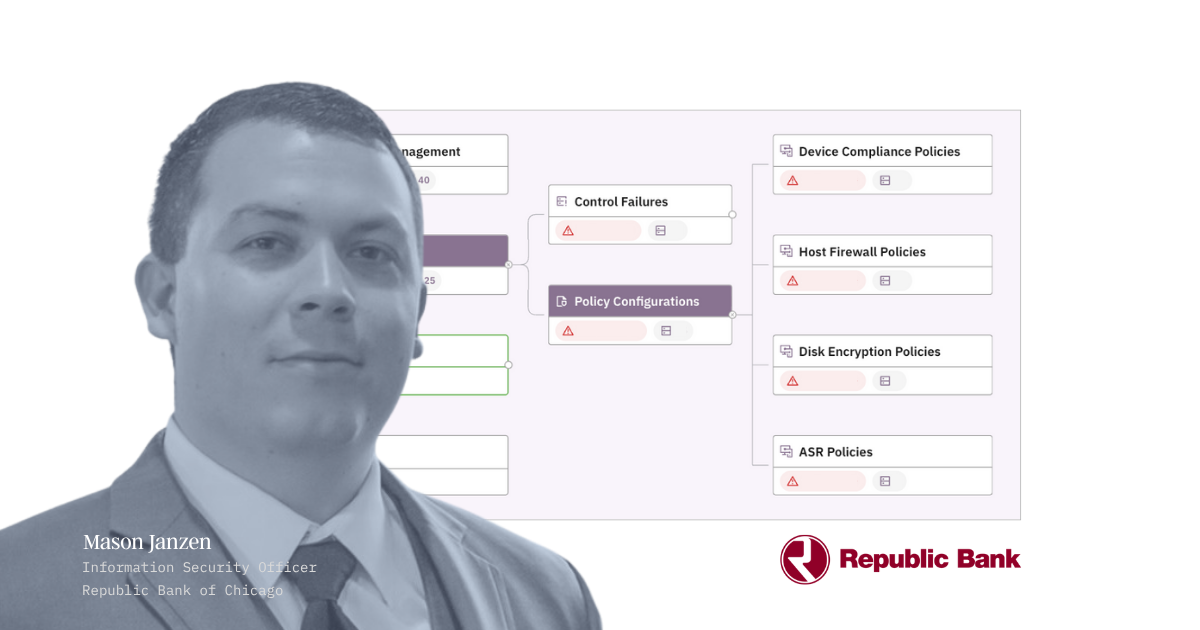
Case studies
Learn how top companies secure their business with Prelude
See for yourself
Don't just read about control validation—try it yourself.
Put our insights to good use with a free trial of Prelude so you can validate the coverage, configuration, and efficacy of your security tools.

.png)