
Endpoint Security
How To Find Endpoints Not Onboarded to Microsoft Defender for Endpoint (MDE)
Discover unprotected endpoints in your Microsoft environment. Step-by-step guide to MDE discovery tools and automated solutions.

Chris Singlemann
Go-to-market
Microsoft
Control Monitoring
Endpoint Security
Email Security
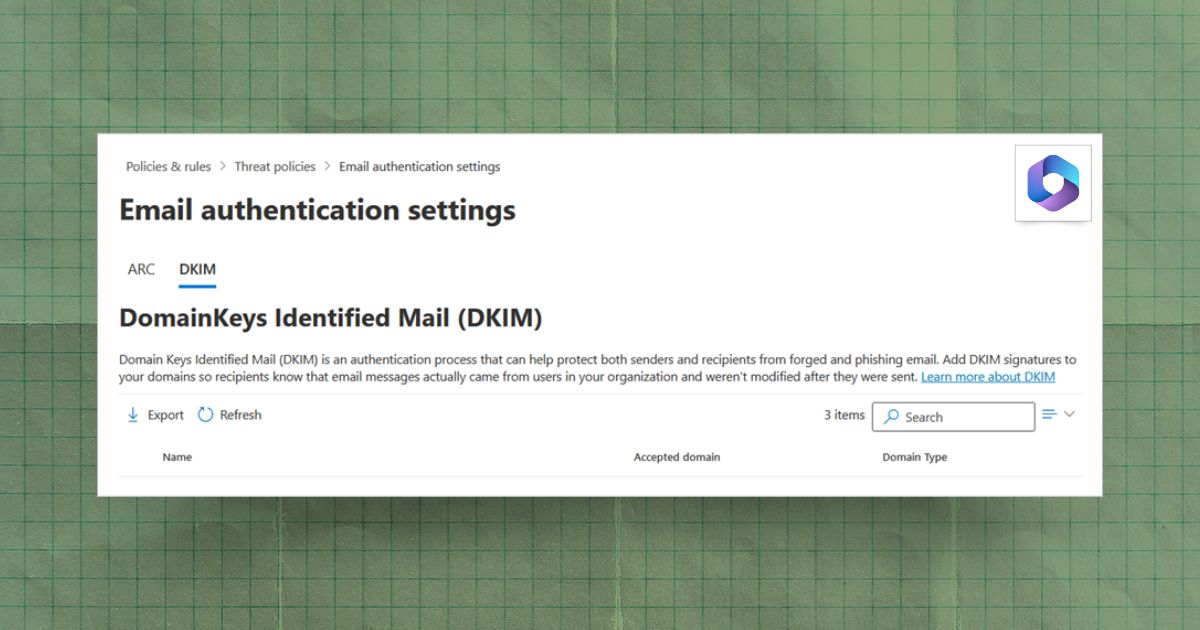
A Configuration Guide to DKIM and DMARC Settings in Microsoft 365
Learn how to configure DKIM and DMARC in Microsoft 365 to prevent email spoofing and improve deliverability. Includes setup steps and monitoring guidance.

Chris Singlemann
Go-to-market
Control Monitoring
Microsoft
Email Security

Endpoint Security
How to Find Unmanaged and BYOD Devices in Your Environment
Learn how to identify unmanaged and BYOD devices using identity logs, MDM systems, and network data to close security gaps and prevent ransomware.

Pete Constantine
Product
Control Monitoring
Risk Management
Endpoint Security

Security
How to Make Cyber Insurance More Than Security Theater
The technical controls required for cyber insurance shouldn't just be about checking the box. Constantly monitoring and validating those tools is the difference between real resilience and your claim not getting paid out.

Spencer Thompson
Leadership
Cyber insurance
Control Validation
Security

Security
The Security Questions You Should Always Be Able to Answer
From device management to MFA enforcement, understanding how your environment is secured at any given time is a critical element for insurance and audits.

Chris Singlemann
Go-to-market
Control Monitoring
Control Validation
Security
Identity Security
Endpoint Security

Endpoint Security
Microsoft Defender Passive Mode: What Is It and How to Use It
Passive Mode is an effective tool in Microsoft Defender Antivirus to manage CPU usage, but only when paired with another active antivirus on the device. Understanding how to find and manage Passive Mode devices is key to ensuring a secure environment.

Chris Singlemann
Go-to-market
Microsoft
Control Monitoring
Endpoint Security

Platform
Introducing Support for Vulnerability Management Tools
Prelude announces foundational integrations with Tenable and Qualys to surface gaps in vulnerability scans that pose risk to security and compliance efforts.

Pete Constantine
Product
Control Monitoring
Vulnerability Management
Platform

Security
How Lean Security Teams Can Build Resilient Defenses
Operationalizing continuous control monitoring and threat exposure management doesn't need to be a drain on your team.

Chris Singlemann
Go-to-market
Control Validation
Control Monitoring
Security

Endpoint Security
A Technical Guide to Volume Shadow Copy Protection in CrowdStrike
Learn how to configure CrowdStrike's Volume Shadow Copy protection to block ransomware from deleting backup snapshots. Includes setup, verification, and monitoring guidance.

Chris Singlemann
Go-to-market
Control Monitoring
CrowdStrike
Endpoint Security
.jpg)
Security Research
Common MITRE ATT&CK Techniques in 2025 UK Retailer Cyberattacks
Explore MITRE ATT&CK techniques used by Scattered Spider in major recent UK retailer cyberattacks and how to evaluate your own organization's defenses.

Garreth Jeremiah
Product
Control Validation
Security Research
Security Testing
Threat Intelligence
Control Validation
Understanding MITRE ATT&CK Mapping: Why It’s Hard—and What You Can Do About It
Mapping your security configuration to frameworks like MITRE ATT&CK can expose coverage gaps and policy miscues, but often requires intensive manual effort.

Joe Kaden
Product
Control Monitoring
Threat Intelligence
Platform
Control Validation

Email Security
How to Maximize Anti-Phishing Settings in Microsoft 365
Email security tools provide a wealth of settings to hone defenses against phishing threats, but knowing whether they're enabled can be a challenge.

Chris Singlemann
Go-to-market
Control Monitoring
Microsoft
Email Security

Security
Better Security Starts With Aggregating Your Asset Inventory
Knowing what to secure is more than half the battle of security. Taking inventory across multiple, disparate security tools often paints an incomplete picture of what exists in your environment.

Pete Constantine
Product
Platform
Control Monitoring
Endpoint Security

Endpoint Security
How to Address Reduced Functionality Mode (RFM) in CrowdStrike
Reduced Functionality Mode (RFM) prevents the Falcon sensor from running expected detection and prevention activities, hampering CrowdStrike's ability to proactively manage threats.

Chris Singlemann
Go-to-market
Control Monitoring
CrowdStrike
Endpoint Security

Platform
What To Do During Your Free Trial of Prelude's Control Monitoring Platform
Finding missing controls, updating critical policies, and evaluating configurations against relevant threats are just some of the ways you can leverage Prelude.

Chris Singlemann
Go-to-market
Control Monitoring
Control Validation
Threat Intelligence
Security
Insights from the SANS Detection and Response Survey
Discover how EDR remains a critical cybersecurity tool, the challenge of talent shortages, and how to make the most of tight budgets.

Chris Singlemann
Go-to-market
Control Monitoring
Control Validation

Control Monitoring
Building a Continuous Threat Exposure Management (CTEM) Program at Your Business
Deploying a robust CTEM program can reduce operational load while mitigating your risk against an increasing number of vulnerabilities.

Chris Singlemann
Go-to-market
Control Monitoring
Security
Security Testing
See for yourself
Done with reading for the day? Try Prelude instead.
Put our insights to good use with a free trial of Prelude so you can validate the coverage, configuration, and efficacy of your security tools.



.jpg)