Endpoint Security
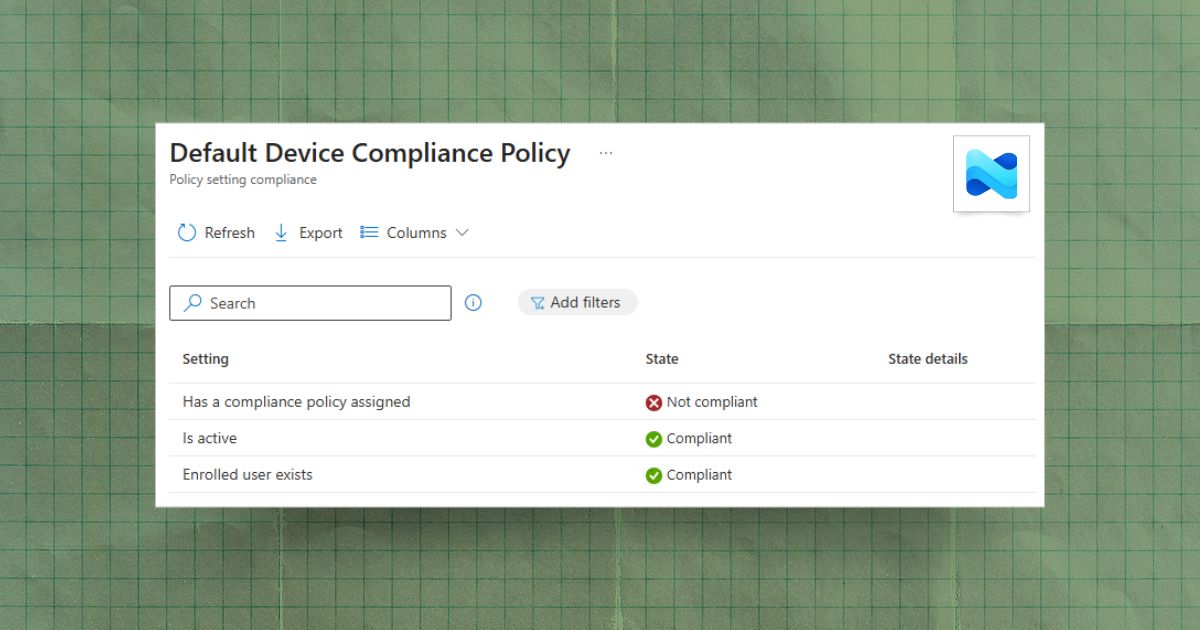
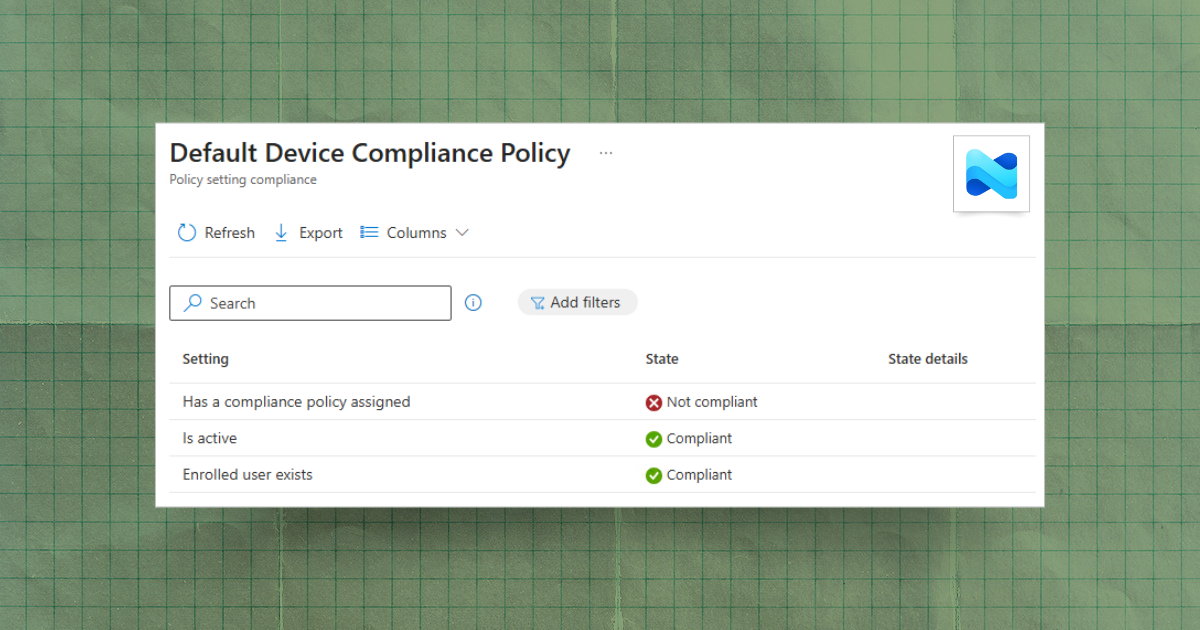
Understanding the Default Device Compliance Policy in Intune
Understand Intune's built-in default device compliance policy, the three checks it enforces, and how to remediate common noncompliant statuses.

Pete Constantine
Product
Microsoft
Control Monitoring
Endpoint Security
Endpoint Security
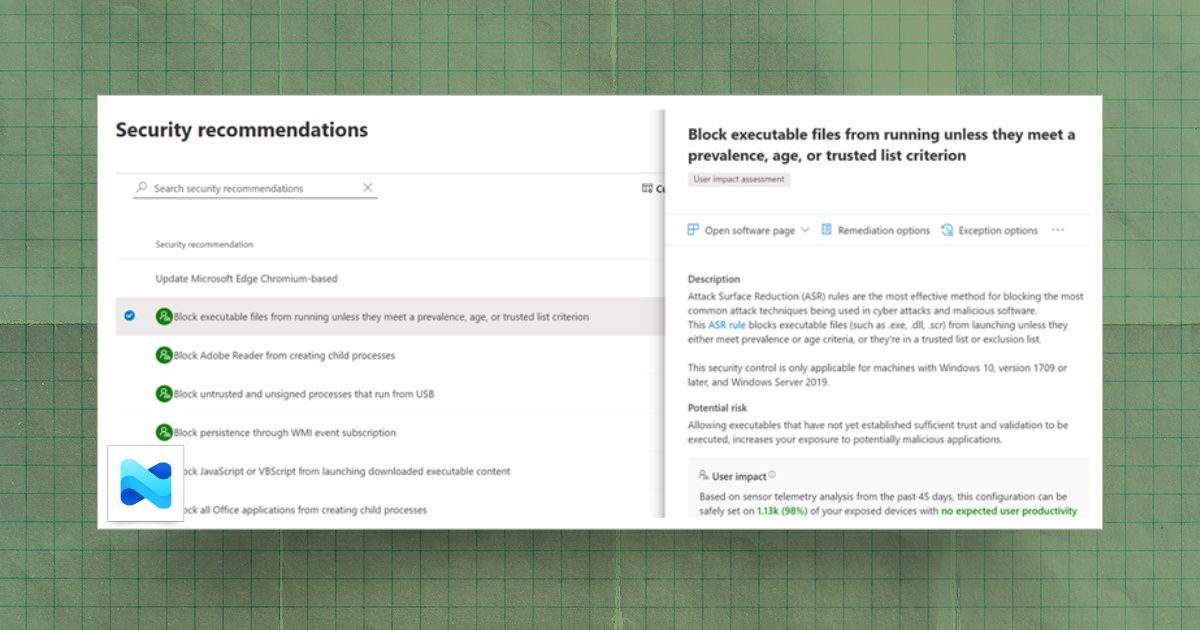
How to Configure Attack Surface Reduction Rules in Microsoft Intune
Step-by-step guide to configuring Attack Surface Reduction rules in Microsoft Intune, from prerequisites to deployment and ongoing monitoring.

Pete Constantine
Product
Control Monitoring
Microsoft
Endpoint Security
Identity Security
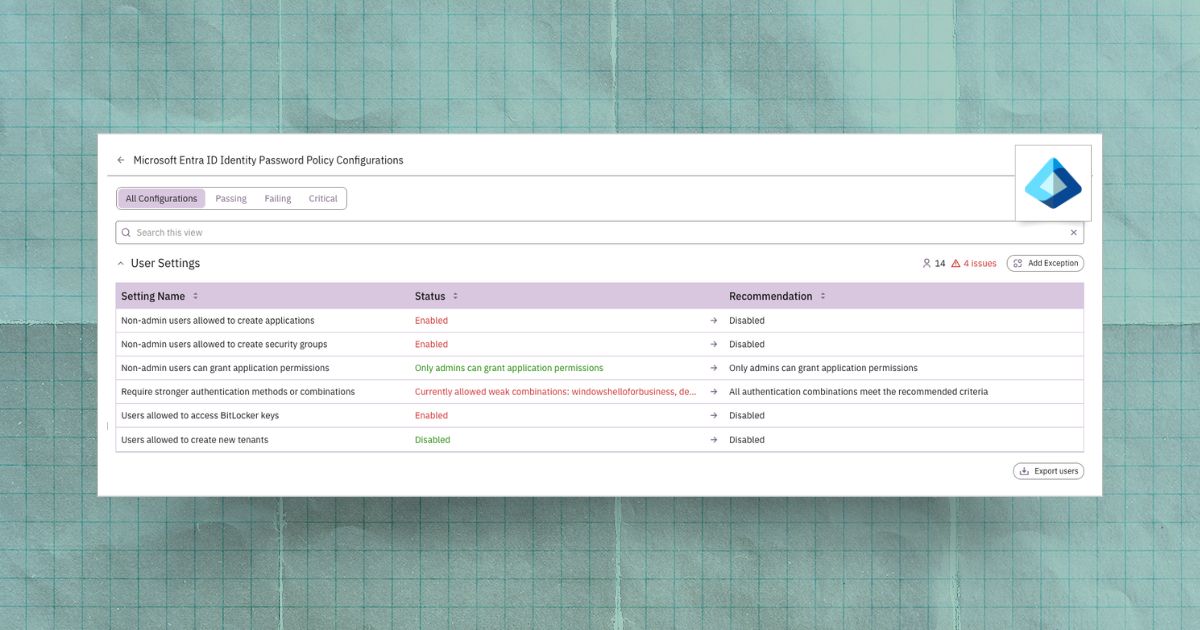
Configuring Entra ID to Prevent User-Created Apps and Security Groups
Learn how to disable risky Entra ID defaults that let users create apps and groups, preventing attacker persistence and shadow IT risks.

Joe Kaden
Product
Control Monitoring
Microsoft
Identity Security
Identity Security
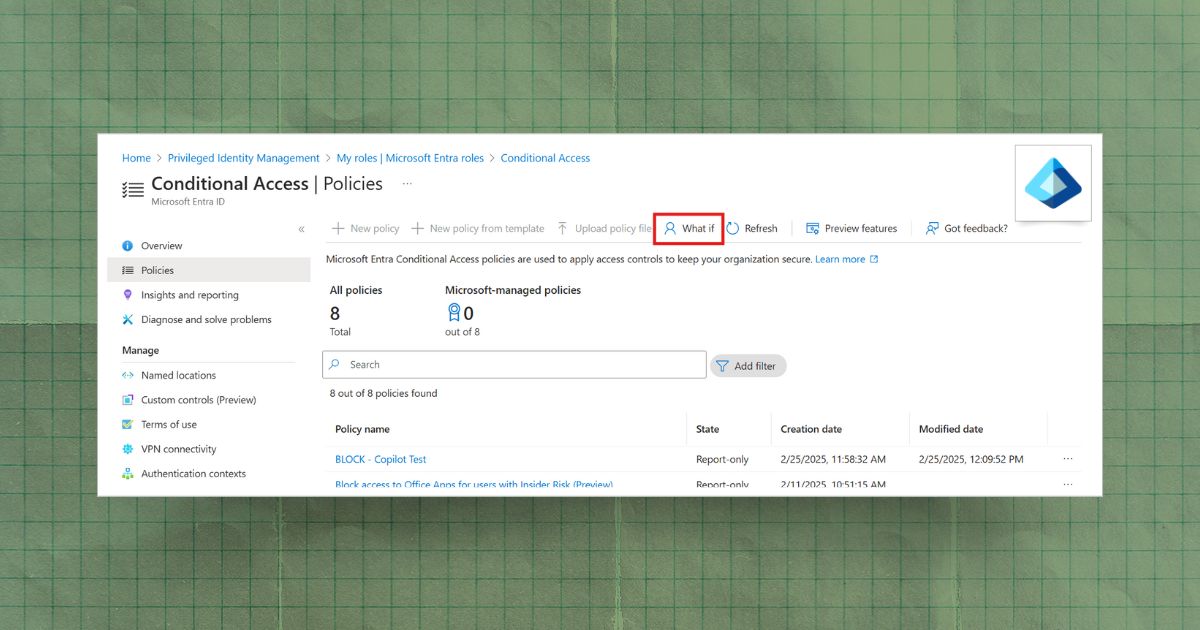
Understanding Conditional Access Policies in Entra ID
Learn how Microsoft Entra ID Conditional Access policies work, common misconfigurations that create security gaps, and how to validate policy enforcement for Zero Trust security.

Joe Kaden
Product
Microsoft
Control Monitoring
Identity Security

Endpoint Security
How To Find Endpoints Not Onboarded to Microsoft Defender for Endpoint (MDE)
Discover unprotected endpoints in your Microsoft environment. Step-by-step guide to MDE discovery tools and automated solutions.

Chris Singlemann
Go-to-market
Microsoft
Control Monitoring
Endpoint Security
Email Security
A Configuration Guide to DKIM and DMARC Settings in Microsoft 365
Learn how to configure DKIM and DMARC in Microsoft 365 to prevent email spoofing and improve deliverability. Includes setup steps and monitoring guidance.

Chris Singlemann
Go-to-market
Control Monitoring
Microsoft
Email Security

Endpoint Security
Microsoft Defender Passive Mode: What Is It and How to Use It
Passive Mode is an effective tool in Microsoft Defender Antivirus to manage CPU usage, but only when paired with another active antivirus on the device. Understanding how to find and manage Passive Mode devices is key to ensuring a secure environment.

Chris Singlemann
Go-to-market
Microsoft
Control Monitoring
Endpoint Security
Resources
Insights to help you manage your security posture
No items found.
See for yourself
Done with reading for the day? Try Prelude instead.
Put our insights to good use with a free trial of Prelude so you can validate the coverage, configuration, and efficacy of your security tools.

.jpg)
.jpg)
.jpg)
.jpg)
