Identity Security
Essential Identity and Access Management Metrics: Definitions, Examples, and Best Practices
Track IAM metrics that matter: MFA coverage, TTDv, JIT access. Get formulas, benchmarks & NIST-aligned targets to measure identity security.

Joe Kaden
Product
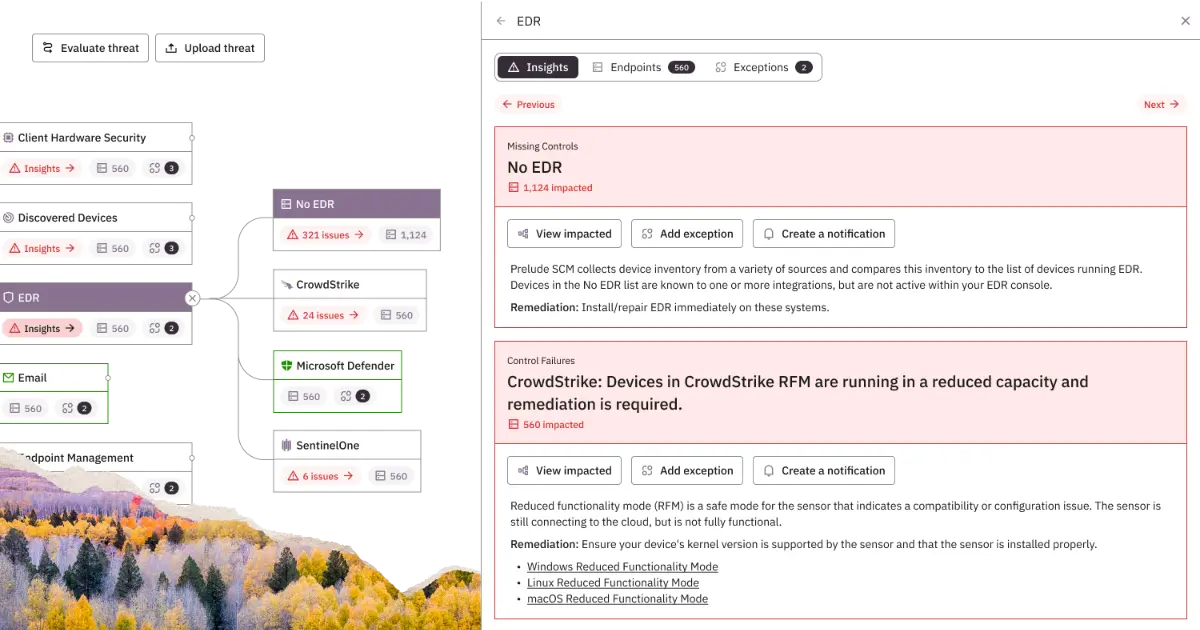
Control Monitoring
Identity Security
Endpoint Security
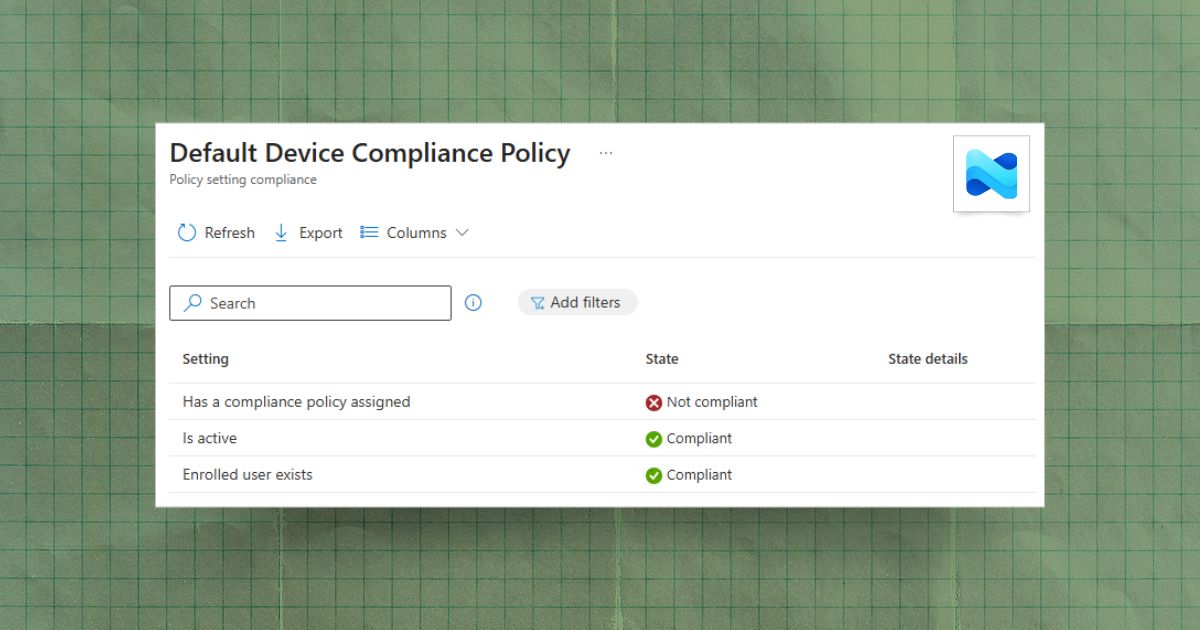
Understanding the Default Device Compliance Policy in Intune
Understand Intune's built-in default device compliance policy, the three checks it enforces, and how to remediate common noncompliant statuses.

Pete Constantine
Product
Microsoft
Control Monitoring
Endpoint Security
Endpoint Security
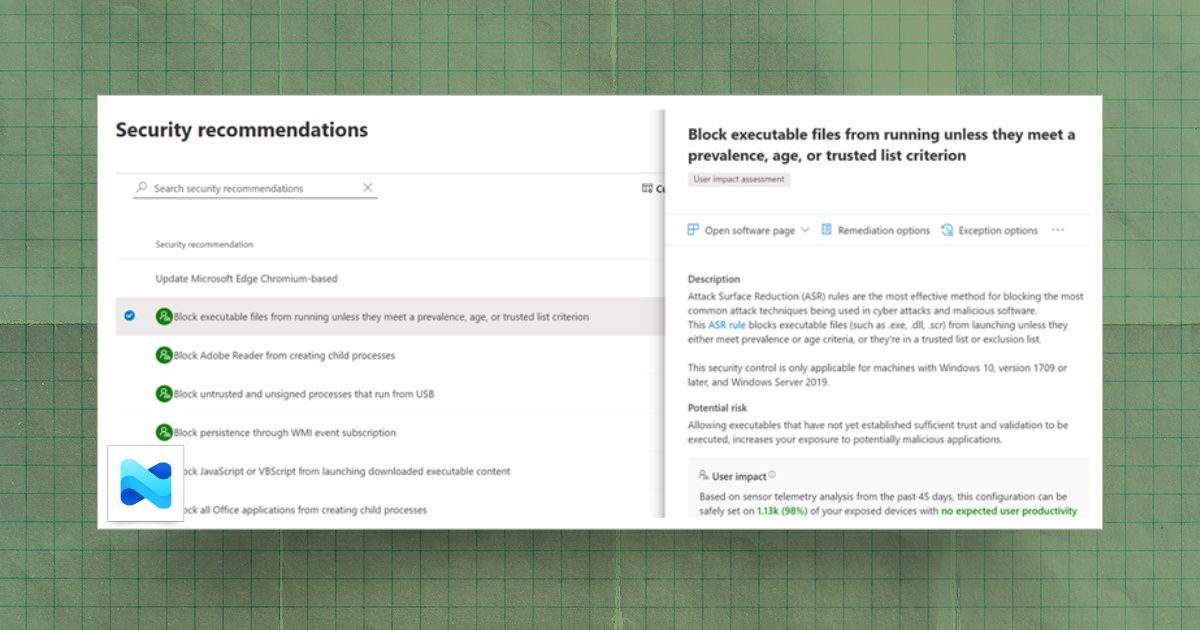
How to Configure Attack Surface Reduction Rules in Microsoft Intune
Step-by-step guide to configuring Attack Surface Reduction rules in Microsoft Intune, from prerequisites to deployment and ongoing monitoring.

Pete Constantine
Product
Control Monitoring
Microsoft
Endpoint Security
Platform
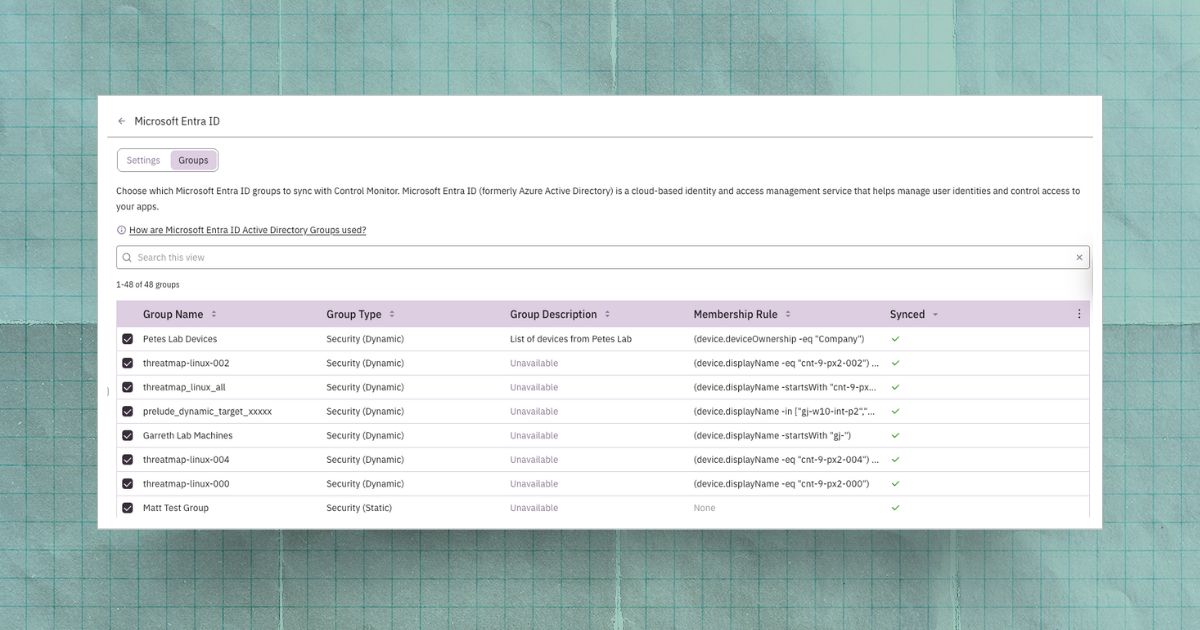
Leveraging Entra ID Groups in Prelude to Visualize Your Security Posture
Sync Entra ID groups with Prelude to visualize security posture by team, filter findings, spot drift, and prioritize remediation where risk is highest.

Joe Kaden
Product
Control Monitoring
Identity Security
Platform
Email Security
Hardening Google Workspace Email: Anti-Spoofing and Advanced Phishing Protections
Learn to configure Gmail's anti-spoofing protections, SPF/DKIM/DMARC authentication, and enhanced scanning to stop phishing attacks.

Chris Singlemann
Go-to-market
Control Monitoring
Google Workspace
Email Security
Identity Security
Configuring Entra ID to Prevent User-Created Apps and Security Groups
Learn how to disable risky Entra ID defaults that let users create apps and groups, preventing attacker persistence and shadow IT risks.

Joe Kaden
Product
Control Monitoring
Microsoft
Identity Security
Identity Security
Understanding Conditional Access Policies in Entra ID
Learn how Microsoft Entra ID Conditional Access policies work, common misconfigurations that create security gaps, and how to validate policy enforcement for Zero Trust security.

Joe Kaden
Product
Microsoft
Control Monitoring
Identity Security

Endpoint Security
How To Find Endpoints Not Onboarded to Microsoft Defender for Endpoint (MDE)
Discover unprotected endpoints in your Microsoft environment. Step-by-step guide to MDE discovery tools and automated solutions.

Chris Singlemann
Go-to-market
Microsoft
Control Monitoring
Endpoint Security
Email Security
A Configuration Guide to DKIM and DMARC Settings in Microsoft 365
Learn how to configure DKIM and DMARC in Microsoft 365 to prevent email spoofing and improve deliverability. Includes setup steps and monitoring guidance.

Chris Singlemann
Go-to-market
Control Monitoring
Microsoft
Email Security

Endpoint Security
How to Find Unmanaged and BYOD Devices in Your Environment
Learn how to identify unmanaged and BYOD devices using identity logs, MDM systems, and network data to close security gaps and prevent ransomware.

Pete Constantine
Product
Control Monitoring
Risk Management
Endpoint Security

Security
The Security Questions You Should Always Be Able to Answer
From device management to MFA enforcement, understanding how your environment is secured at any given time is a critical element for insurance and audits.

Chris Singlemann
Go-to-market
Control Monitoring
Control Validation
Security
Identity Security
Endpoint Security

Endpoint Security
Microsoft Defender Passive Mode: What Is It and How to Use It
Passive Mode is an effective tool in Microsoft Defender Antivirus to manage CPU usage, but only when paired with another active antivirus on the device. Understanding how to find and manage Passive Mode devices is key to ensuring a secure environment.

Chris Singlemann
Go-to-market
Microsoft
Control Monitoring
Endpoint Security

Platform
Introducing Support for Vulnerability Management Tools
Prelude announces foundational integrations with Tenable and Qualys to surface gaps in vulnerability scans that pose risk to security and compliance efforts.

Pete Constantine
Product
Control Monitoring
Vulnerability Management
Platform

Security
How Lean Security Teams Can Build Resilient Defenses
Operationalizing continuous control monitoring and threat exposure management doesn't need to be a drain on your team.

Chris Singlemann
Go-to-market
Control Validation
Control Monitoring
Security

Endpoint Security
A Technical Guide to Volume Shadow Copy Protection in CrowdStrike
Learn how to configure CrowdStrike's Volume Shadow Copy protection to block ransomware from deleting backup snapshots. Includes setup, verification, and monitoring guidance.

Chris Singlemann
Go-to-market
Control Monitoring
CrowdStrike
Endpoint Security
Control Validation
Understanding MITRE ATT&CK Mapping: Why It’s Hard—and What You Can Do About It
Mapping your security configuration to frameworks like MITRE ATT&CK can expose coverage gaps and policy miscues, but often requires intensive manual effort.

Joe Kaden
Product
Control Monitoring
Threat Intelligence
Platform
Control Validation

Email Security
How to Maximize Anti-Phishing Settings in Microsoft 365
Email security tools provide a wealth of settings to hone defenses against phishing threats, but knowing whether they're enabled can be a challenge.

Chris Singlemann
Go-to-market
Control Monitoring
Microsoft
Email Security

Security
Better Security Starts With Aggregating Your Asset Inventory
Knowing what to secure is more than half the battle of security. Taking inventory across multiple, disparate security tools often paints an incomplete picture of what exists in your environment.

Pete Constantine
Product
Platform
Control Monitoring
Endpoint Security

Endpoint Security
How to Address Reduced Functionality Mode (RFM) in CrowdStrike
Reduced Functionality Mode (RFM) prevents the Falcon sensor from running expected detection and prevention activities, hampering CrowdStrike's ability to proactively manage threats.

Chris Singlemann
Go-to-market
Control Monitoring
CrowdStrike
Endpoint Security
Resources
Insights to help you manage your security posture
See for yourself
Done with reading for the day? Try Prelude instead.
Put our insights to good use with a free trial of Prelude so you can validate the coverage, configuration, and efficacy of your security tools.


.png)